
The Independent HP NonStop(tm) eNewsletter
From Tandemworld for May 2017
Platinum Sponsor is
Gold Sponsor
Silver Sponsor
Tandemworld eNewsletter
for May 2017
Contents New Innovations
from NTI Get
the Latest on What's New in NonStop from NuWave XYPRO - Get
Smart! Control KAOS with Layered Security
HPE Publishes Shadowbase BASE24 Success Story at
Cartu Bank Availability Digest Says That
Before You Start Worrying about Y2038, Get Scared about Y2028
Old Friends, Familiar Faces, New Acquaintances
Have a Crisis?
OmniPayments’ OmniCloudX is World’s First Cloud Built on NonStop X
eBITUG 2017, London
- For Your Eyes Only
TANGO’S NATIVE ANTI-FRAUD
FEATURES REPORT XYPRO Team Profiles: Support Guru
Leads Layer8 to CCDC Nationals
comForte eBITUG Video - Keeping your data 'For yo#2 636&
only’ Part I Smashing
Silos- Tributary Systems Storage Director and Cloud Object Storage
XYPRO looks forward to seeing you at the upcoming shows! ASK
comForte
- eBook on Modernizing Applications on the NonStop Platform
“Event-full” times
for DataExpress
comForte events near you:
Registration for the
2017 NonStop Technical Boot Camp is OPEN!
Current Subscribers 15127
New Innovations from NTI
On Tuesday May 9th in London NTI announced two new product offerings at the eBITUG conference.
EVOLUTION provides a fabric for the seamless migration of GoldenGate systems to the new Xbox. Evolution is truly a revolutionary approach to platform migration. Beyond the evolution fabric NTI has assembled analysis, support and migration solutions that surround Oracle GoldenGate installations and ensures a successful seamless migration.
Web content for EVOLUTION is online at
(https://network-tech.com/Evolution.php).
VISION provides a way to use the data flowing thru your NonStop for new analytics and applications. VISION is so new that our web content is not yet online. In the coming months expect additional announcements that will WOW you.
You can download and view the London announcement and presentation at
DRNet® is world class NonStop Data Replication technology.
· Real-time Active/Active Data Replication
· Real-time Tandem to OPEN Data Replication
· Real-time File Synchronization
· Refreshingly Real-Time Support from Real Engineers
+1 (402) 968 3674
Get the Latest on What's New in NonStop from NuWave
NuWave's NonStop Innovations blog is dedicated to bringing the community the latest in NonStop news, trends and technology.
There are some great articles coming up from some of the best minds in NonStop.
Visit it today and be sure to subscribe for future notifications!
XYPRO - Get Smart! Control KAOS with Layered Security


I recently came across reruns of a TV show from the 60’s called “Get Smart”. In the opening sequence of the show, the lead character, Maxwell Smart, played by Don Adams, must pass through nearly a dozen doors, or layers of security in order to access his job at “Control” where the secrets are stored.
I spend a lot of time discussing security strategy and requirements with colleagues, customers and the NonStop user community in general. Over the last 10 years that I’ve been working in the NonStop space, it’s become clear that the traditional approach to security – applying a single layer of security or a solution that meets a certain requirement, has some serious shortcomings. History has shown time and time again that although a single focused solution can be useful in stopping a particular attack, in the long run, more patient and advanced adversaries will find this approach to security merely an inconvenience. I’m amazed at how often I hear “That’s good enough for us” speaking about a particular approach.
“We use multi-factor
authentication.”
“We use encryption.”
“We scan our systems.”
“Our servers aren’t connected to the internet.”
“Our auditors have not mentioned that.”
No one is suffering from the illusion that there’s a silver bullet that will effortlessly make an organization 100% secure. More importantly, the perimeter itself is dissolving. Punting security to an external group and relying on firewalls, IDS/IPS and authentication controls by themselves to protect a system is irresponsible and actually leaves unexpected holes in the system. Identifying your assets and building your security strategy around those assets is the only true way to mitigate risk. Identification is key. If you don’t know what you are protecting and why you are protecting it, it becomes difficult to deploy the right security measures.
Layered security takes the military concept of “Defense in Depth” and applies it to cyber security. The idea is simple; a single solution may stop a certain type of attack, but if an attack does get through, the layers behind them are set up to continuously slow down and stop the attacker. For example, a castle may have a moat, a protected door, a perimeter wall, guards and guard towers, inner walls and a highly secure, highly protected safe that contains the crown jewels. The same strategy should be applied to how critical digital assets are secured.
Hardening the NonStop server is no different. Structure your security solutions to best manage your risk. The goal is if an attack gets past a single layer or solution, the subsequent layers are purposefully set-up to slow down and narrow the field of attack.
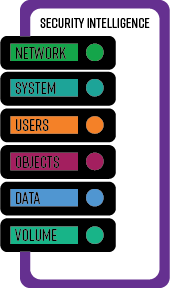
XYPRO’s approach to HPE NonStop security is this: we took the same layered, defense in depth strategy and deconstructed all those layers to identify where the system or data is most at risk on the NonStop server. We apply the strategy based on the risk involved, the type of data we’re aiming to protect, and how different layers can interact with each other for risk mitigation. We ended up with the layers illustrated below. In this introductory article, we’ll identify and explain all the layers. In future articles we’ll discuss the importance of each layer in depth.
The Network Layer
![]()
The Network layer is the outermost layer of the system and most likely to be targeted first. This layer is essentially your system’s perimeter, where applications are exposed and data is in motion, communicating with other systems and endpoints. Unlike subsequent layers, the system does not necessarily need to be compromised for an attack to be successful at this layer. Therefore, it’s critical to ensure all data flowing in and out of the system at this layer is properly protected using secure protocols such as TLS, SSH, SFTP etc.… and ensuring no suspicious ports or services are available for external fingerprinting or other reconnaissance activity. Implementing security at this layer will cause a potential attacker to look elsewhere.
The System Layer

The system layer controls who is allowed to have access into your system. This is where logon controls are set up, credentials are validated and additional integrations, such as Multi-factor Authentication and other authentication providers are implemented. An often overlooked but equally important understanding is access isn’t only for users or logging into the system. Processes, objects and subsystems also need to properly authenticate themselves to access system resources and data. Think of this layer as the front door to your house. A thief would typically need valid credentials, or keys, to proceed any further. Although hardening your defenses here is a must, assume a motivated and patient adversary will bide their time and eventually get the keys they are looking for. And not to mention those pesky insider threats who may already have validated access to the system. How do you slow them down once they penetrate this layer?
The User Layer
The user layer approach takes the position that users shouldn’t have unchecked permissions on a system, even after they’ve been granted access. Assume an attacker was road blocked at the Network Layer, but was able to compromise a user’s credentials at the system layer and logged on to the system. Deploying a proper layered strategy at these next two layers will ensure access to the “Data in Use” is properly controlled and managed. Once granted access to a system, users shouldn’t have free reign to browse and run applications and utilities as they please (although I have seen this happen more than I’m comfortable admitting). Controlling what a user can access in terms of utilities and system locations based on their role, job responsibilities and other factors is a critical approach to executing a proper security strategy. Role Based Access Control (RBAC) is a familiar concept to most security administrators. RBAC is deployed at this layer.
Let’s look at an example. Your organization has a database administrator who should only have access to SQLCI and no other applications or utilities for their job function. Using RBAC, you restrict their access to the utility needed to execute their job duties and deny access to everything else. That way, if their credentials are compromised at the system layer, their ability to access utilities and programs will be tightly controlled. It is very important to note as part of this process, that their access be monitored via proper audits. We’ll discuss this later.
XYPRO’s XYGATE Access Control (XAC) can take RBAC a step further, by restricting control to the subcommand level within utilities and programs. So, unless a user is explicitly granted access to run a utility or program, or even a subcommand within a utility, they will be denied. Further controlling what a malicious user may or may not do if they get down to this layer
The Object Layer
The object layer will ensure access to resources is granted only to authorized users. Resources may include files, volumes, subvolumes, databases and other objects. Building on the previous layer that restricted access based on actions, protection at the object layer will ensure an authorized user running an authorized application can only access authorized objects.
The Data Layer
The data layer is where the core of your data resides. The crown jewels of what an attacker would be after. Examples of these would be data stored within files, databases and other data repositories containing critical business data, payment card data, customer data and other critical data necessary for your operations. This is typically referenced as “Data at Rest”. If an attacker made it this far, your last line of defense would be to make the data completely unrecognizable. There are several solutions that exist such as HPE SecureData Transparent Data Protection encryption solutions. These solutions will tokenize or encrypt data at rest, so even if the data was exfiltrated, it would be of no use to the thief.
The Volume Layer

To protect the volume layer, often considered a physical layer of security, HPE offers solutions that protect data at rest at the disk level. One solution is Volume Level Encryption (VLE). An important point to keep in mind, VLE only protects against physical threats. If someone were to walk into your data center and walk out with a hard drive containing critical data, using VLE, that drive would be unusable to them. VLE does not protect application access to the data once the system is on and running. This concept shifts around a bit in the vNonStop world, but the objective is still the same.

Audit and Monitoring
Implementing controls without auditing and monitoring is ineffective and can ultimately be the Achilles heel that sinks a security strategy. Generating audit records at every layer for critical activities and reviewing those in a timely fashion will help gain insight into a security strategy like never before. Security intelligence and analytics are no longer buzzwords. Solutions like XYGATE SecurityOne® (XS1) and other analytics platforms can give you views into your data and what is happening on your systems like never before. What was traditionally a very tedious and time consuming activity with little result can tilt the scale in your favor and slow down or even stop a costly breach. At the end of the day, data is king. You can add defenses at every layer, but without generating the data to know what is happening at those layers, you’re flying blind and cannot ensure your defenses are working the way you intended. As part of this process, ensure the operating systems and applications are patched and updated regularly.

Back to Get Smart…… The reason I found the TV show so relatable to this article (aside from the very appropriate title) is the character works for a secret U.S. government counter-intelligence agency named CONTROL which is appropriate to all of the differing security layers for controlling access to computers and their data. CONTROL’s nemesis is KAOS who are an international organization of evil and represent the chaos of all the various threats against computers and their data. The fit was perfect with the opening to the show depicting agent 86 passing through many layers of security protecting their secrets and intelligence information. Agent 86, with his many layers of security, provide him with a 100% success record of detecting and averting disasters.
A motivated attacker will always find a way. Using a layered security approach to risk management can slow their advances enough to allow you to counter their moves. Without a strategy in place to address what happens when they get through, you are gambling, and hoping an attack will stop once they hit the first obstacle you throw at them.
Technology continues to evolve. The skill level & creativity of attackers also continues to evolve. Organizations and merchants need to up their game and their security strategy to keep up with the challenges of the current landscape. This not only benefits the organization, but more importantly provides the necessary assurance to customers that their critical data is being responsibly handled and protected in the most secure way possible.
We’ll be taking a deeper dive into the importance and risk at each layer in upcoming blogs and articles and discuss how to map solutions to set up your strategy to best mitigate your risk. Stay tuned!
Steve Tcherchian
Chief Information Security Officer
XYPRO
Technology
HPE Publishes Shadowbase BASE24 Success Story at Cartu Bank
Last month, HPE published a new case study, Cartu Bank ensures continuous availability of payment services for Georgian businesses.
Cartu Bank understands the need for continuous availability with more than 60% of all e-commerce transactions in the Eastern European country of Georgia going through its payment switch. Read how HPE NonStop servers with HPE Shadowbase software run mission-critical BASE24 payment engines to keep the Georgian economy running 24x7. Giorgi Ioramashvili, head of Cartu Bank’s IT department, remarks, “It was important to our solution to have replication software like Shadowbase integrated with the NonStop servers. We looked at Oracle GoldenGate, which also could replicate BASE24, but because Shadowbase operates natively within the NonStop operating environment, it was more stable and easier to work with. Plus, Shadowbase was 40% to 50% less expensive than Oracle GoldenGate.”
Gravic Presents on HPE Shadowbase Synchronous Replication at
eBITUG, MRTUG, and OTUG

We recently presented on our new product, HPE Shadowbase Zero Data Loss (ZDL) at eBITUG, held in Tower Hill, London, and at MRTUG (Chicago) and OTUG (Columbus, OH). We are excited and proud to bring this new product to market, which requires the implementation of many novel (patented) techniques. Attendees enjoyed learning more about new HPE Shadowbase features, including the pros and cons of asynchronous versus synchronous replication; the feature’s rollout sequence; architectural flow; and what to consider when using synchronous replication. Please contact us, if you think that you could benefit from this technology or are interested in learning more or having us present it to your colleagues.
We want to thank the local HPE team for meeting with Xypro, Idelji, and Gravic at the Partner Technical Update prior to eBITUG; the CSP Team for the unforgettable evening at Aqua Shard; and Collin Yates from TCM and the eBITUG committee for organizing a successful show. Congratulations to Wolfgang Breidbach of BV Zahlungssysteme GmbH, who won our gift card prize at eBITUG!
Gravic Introduces HPE Shadowbase to South American Markets
In April, we traveled to South America to present on HPE Shadowbase solutions at enthusiastic regional user group meetings in Santiago, Chile; Buenos Aires, Argentina; and Bogota, Colombia. We described how Shadowbase works in various solution categories: business continuity (active/passive through active/active), data integration and synchronization, application integration, various utility ancillary products, and demonstrated several use cases. HPE field teams enjoyed and benefitted from our product suite update presentations at PTUs held in Santiago and Bogota.
To speak with us about your data replication and data integration needs, please visit us at www.ShadowbaseSoftware.com, email us at SBProductManagement@gravic.com, or call us at +1.610.647.6250. Hewlett Packard Enterprise directly sells and supports Shadowbase solutions under the name HPE Shadowbase. For more information, please contact your local HPE account team or visit our website.
Please Visit Gravic at these Upcoming 2017 Events
|
NYTUG Meeting—Berkeley Heights, NJ, 25 May |
|
|
|
N2TUG Meeting—Dallas, 1 June |
|
|
|
MATUG Meeting—TBD September |
|
|
|
MEXTUG Meeting—TBD September |
|
|
|
ATUG Meeting—Atlanta, 20 September |
|
|
|
CTUG Fall Conference—Toronto, TBD October |
|
|
|
Connect HPE NonStop TBC—San Francisco, 13-15 November |
Availability Digest Says That Before You Start Worrying about Y2038, Get Scared about Y2028
Here we go again - yet another future-date issue with which some of us need to take notice. In addition to the Year 2038 Unix Millennium Bug that may cause remaining Unix 32-bit operating systems to crash, now we have the Year 2028 Bug for companies that resolved their Y2K issues with a quick-fix remediation.
As the year 2000 approached, businesses worldwide struggled to modify their applications to accommodate a four-digit date field instead of a two-digit date field. Those modifications were costly and took time. For companies that began their Y2K efforts late or that found their endeavors to be cost-prohibitive, makeshift solutions were created.
One clever remedy was based on the knowledge that the Gregorian Calendar repeats itself every 28 years. “What if,” someone asked, “we subtract 28 years from 1999? That gives us the year 1971, and all the days of the week in 1971 are identical to 1999. April 1, 1971, fell on a Monday as did April 1, 1999. December 25, 1971, fell on a Saturday as it did on December 25, 1999. Therefore, by subtracting 28 years from 1999 and every subsequent year, companies still could use their two-digit date fields accurately. All they had to do was to program applications to add 28 years for any forward-date testing. In the year 2017, such applications are set to the year 1989.
Next comes the stroke of Midnight on January 1, 2028. Two-digit applications will display 00; and just like what happened on January 1, 2000, applications will read the year as 1900. The fix? Throw those applications away, or rewrite them; but don’t assume that such applications no longer will be in use.
In addition to “Not Only the Y2038 Problem – There’s a Y2028 Problem,” read the following articles in the Availability Digest’s May 2017 issue:
Testing for Y2038 and Y2028 – This companion article to “Not Only the Y2038 Problem – There’s a Y2028 Problem” discusses the need to test applications, especially legacy applications, for their vulnerabilities to Y2038 and Y2028. Among the testing tools mentioned is OPTA2000 from TANDsoft Inc., an HPE Nonstop partner. www.tandsoft.com
Internet Disruptions – A recent survey by Spiceworks and hosted by Dyn focused on the impact that an Internet-service disruption can have on an organization. Included within the survey were over 200 IT decision makers in companies with 1,000 employees or more. Findings indicated that nearly all companies suffered an outage within the last year and can anticipate another Internet outage in the next six months.
Yahoo’s Users Are Victims of Massive Hacks – Industry analysts have said for years that Yahoo’s one-billion user accounts makes it a prime target for hackers. Obviously, hackers agree. Major Yahoo hacks have occurred in 2013, 2014, and 2016. Those in 2013 and 2014 are the largest known security breaches of any one company’s computer network. How do Yahoo users protect their accounts? Security experts offer several suggestions.
@availabilitydig – The Twitter Feed of Outages - Our article highlights some of our numerous tweets that were favorited and retweeted in recent days.
Digest Managing Editor Dr. Bill Highleyman will present “How ‘Fat” Are Your Fingers” at NYTUG on May 25th in Berkeley Heights, New Jersey (USA). http://bit.ly/2qAHjFY
The Availability Digest offers one-day and multi-day seminars on High Availability: Concepts and Practices. Seminars are given both onsite and online and are tailored to an organization’s specific needs. Popular seminars are devoted to achieving fast failover, the impact of redundancy on availability, basic availability concepts, and eliminating planned downtime.
In addition, the Digest provides a variety of technical writing, consulting, marketing, and seminar services. For instance, many articles that you see in publications like The Connection were ghostwritten by us for individuals too busy to write themselves. We also create white papers, case studies, technical manuals and specifications, RFPs, presentation slides, web content, press releases, advertisements, and so on.
Consider us as well for the following:
• Patent Disclosures – Dr. Bill Highleyman is the holder of a dozen-plus patents and will be happy to help you with your applications.
• Book Writing – As the author of “Performance Analysis of Transaction Processing Systems” and a co-author of the three-part series “Breaking the Availability Barrier,” Dr. Bill understands the effort it takes to produce a manuscript.
• Consulting – We specialize in system architectures and risk analyses that help our customers provide the appropriate uptime, performance, and data protection for individual applications.
Published monthly, the Digest is free and lives at www.availabilitydigest.com. Please visit our Continuous Availability Forum on LinkedIn. We’re at 793 members and counting. Follow us as well on Twitter @availabilitydig.
Old Friends, Familiar Faces, New Acquaintances
Perusing all the post eBITUG feedback, it’s fair to say that it was a great success and therefore, many thanks are due to the BITUG Committee for their excellent event planning and to CSP for a magnificent evening hosted at the Shard.
Karl Gilbank, Insider Technologies Sales and Marketing Director experienced his first “Tandem User Group” and it was an invaluable opportunity for him to meet and greet our fabulous customers including as the Bank of England, Euroclear, Deutsche Bank, Barclays Bank, Standard Chartered Bank and HSBC.
Thanks also for new introductions and shared insights with ING Bank, Vocalink, WorldPay, and FirstData, amongst many others.
The enthusiasm with which HPE addressed the planned roadmap for NonStop gives the community much to be positive about. Mobile monitoring, virtualization, and private + public cloud solutions are ensuring the development of new applications that improve efficiencies and reduce risk in the Enterprise sector.
Equally exciting is the growing propensity to leverage complimentary solutions through partnership. As companies seek expansion in to growing markets such as Central & South America, Japan, and South Korea, technology firms are more open to creating joint propositions that offer great value to the market. Insider Technologies is an advocate of this approach, and we were pleased to have had some excellent engagement with many of outstanding firms that share the NonStop space.
The overall take away was one of confidence in the continued importance of NonStop as a core piece of infrastructure in some of the world’s most demanding markets. Insider Technologies is committed to continually innovating new and improved solutions to assist the Tandem User Group.
Have a Crisis? All Your NonStop Guys Retired? No Worries with BrightStrand’s Flexible Resource Program


It is a sad fact of life in the NonStop world. Your NonStop Systems work forever, but your developers and support teams don’t. They retire, they migrate to other assignments, and their expertise is difficult to replace in your business-critical environment. That is why you count on BrightStrand International and its flexible resource program. Brought to you by the largest pool of HPE NonStop resources in the U.K. and quite possibly in the world.
Here is how our flexible resource program works.
Not every company requires a year’s worth of support services. So why pay for a year’s worth? With BrightStrand, you have the option of contracting for a predetermined number of service days over a defined period. That way, all contractual necessities are in place. When an emergency or another unforeseen issue arises, we can act quickly to place the most appropriate resources at work on your behalf. You avoid having to negotiate prices and terms while your systems – and your business – suffer.
Your costs are less than those of an annual contract, and you can add more days if necessary.
Beyond the obvious advantage of having access to our highly experienced NonStop team, BrightStrand’s flexible resource program allow us the opportunity to understand your system configurations and applications. Therefore, well in advance of your use of our services, we can anticipate the skills you may need and which of our BrightStrand colleagues are best suited to assist you.
Just how far-reaching are BrightStrand’s skillsets? When it comes to NonStop, we have centuries of combined experience spanning every NonStop platform and operating system. Our multiplatform support extends as well to IBM, UNIX, and Windows. Count on us to be prepared for any challenge your systems encounter because we have experienced every possible challenge.
Such deep expertise is a valuable commodity. What it offers BrightStrand customers is peace of mind.
BrightStrand International is your go-to source for highly skilled IT professionals. In addition to our flexible resource program, BrightStrand offers a complete product lifecycle from initial planning through implementation to fully managed services. We work onsite and remotely, and everything we undertake is tailored to the specific requirements of each customer. The result? Lower costs, reduced risk, higher availability and increased efficiencies.
We encourage you to contact us for additional information.
Tel: +44(0)141 204 4046
Email: info@brightstrand.com
OmniPayments’ OmniCloudX is World’s First Cloud Built on NonStop X
Someone had to be the first! In the case of a cloud built on NonStop X, we’re happy to say it was OmniPayments. Our OmniCloudX hosts numerous instances of the OmniPayments Financial Transaction Switch at a price so attractive that mid-size financial institutions and retailers now can afford their own high-capacity financial transaction switches at a pay-as-you-go price.
So popular is OmniCloudX that our newest cloud customers are large banks and merchants seeking a cloud-based switching solution on NonStop’s legendary mission-critical platform. The added advantage is that OmniPayments is an experienced 24x7 managed services provider for remote production monitoring. OmniCloudX customers save themselves the time and expense of having to learn and maintain the NonStop system because OmniPayments does it for them. In the process, we are introducing new customers to HPE NonStop.
OmniCloudX is
• Highly scalable
• Continuously available with automatic failover to our other NonStop X systems
• Secure and supplies complete security functions for every financial transaction handled
• Supports a range of disaster-recovery solutions
• Affordable. Each OmniCloudX customer pays only for the CPU resources, storage, and networking that it uses
• Able to survive any single fault
• Easily expandable to provide additional functionality when needed
• Requires no downtime for maintenance or upgrades
The OmniPayments Financial Transaction Switch is a switching solution for the financial and retail industries. It is deployed on NonStop for the highest availability and offers all the requisite functionality to manage credit/debit-card transactions. It manages multiple devices, hosts application interfaces, and interoperates with third-party products or other systems if required. OmniPayments easily expands to provide additional functionality when needed and supplies complete security functions for every financial transaction handled, including encryption-at-rest and encryption-in-flight.
OmniPayments can be installed either as a complete, off-the-shelf solution or can be enhanced with customer-requested modifications and features to improve cost-effectiveness, efficiency, and risk mitigation. We offer a wide range of separately sold microservices that connect seamlessly to your other systems and solutions.
OmniPayments systems in production today process 1 billion transactions per month via ATMs, point-of-sale terminals, and mobile applications. A single OmniPayments system can support up to 10,000 transactions per second. Multiple OmniPayments systems can cooperate to provide any capacity required by an application. We have seven locations worldwide.
Where in the World Are Yash and Jessica?
Jessica Nieves, our Vice President of Client Services, will discuss OmniCloudX at NYTUG (Berkeley Heights, NJ USA) on 25 May 2017 and at N2TUG (Grapevine,Texas USA) on 1 June 2017. Find out more about both events at http://www.connect-community.org/chapter-events-2017.
Jessica will join OmniPayments CEO Yash Kapadia for customer meetings at Discover (Las Vegas, Nevada USA) on 6-8 June 2017. Contact either Jessica or Yash to arrange a meeting during the event. jessica@omnipayments.com yash@omnipayments.com


Jessica Nieves Yash Kapadia
Vice President, Client Services CEO
Jessica@omnipayments.com yash@omnipayments.com
To learn more about OmniPayments, contact Yash Kapadia at +1 408-446-9274 or at yash@omnipayments.com. OmniPayments customers and others interested in our solutions are invited to join the OmniPayments Discussion Group on LinkedIn at http://bit.ly/2bB1AGh.
eBITUG 2017, London - For Your Eyes Only

The European NonStop User community travelled to London for the eBITUG conference which was held at the DoubleTree Hotel in Tower Hill. A total of 266 attendees – customers, vendors and HPE delegates - showed up which, I believe, is a record number for the European event. So, well done to the BITUG committee for putting on a successful show!
The highlight of the first day in many ways was the keynote speech given by no other than Jimmy Treybig, founder of Tandem Computers in 1974 and Venture Capitalist.
He gave an insight in what it takes to implement/instigate/initiate change in an organization or even an industry – courage and patience (and some luck). Another key element in driving change is sharing your strategy and vision with staff and key stakeholders in order for people to understand and to make the journey with you.
According to Jimmy, in order to make any business successful you need to put your customers and customer satisfaction first. At Tandem, this was key – as many will remember – and with it the legendary Tandem Culture which was built on trust and respect.
If it wasn’t for people like Jimmy taking the opportunity (and the risk) when they did we all would not be in this much valued NonStop business of ours. Quite an impressive thought!
The second keynote of the day was by Andrew Bergholz, Senior Director NonStop Engineering, and he talked about the Future of NonStop and mapped out the journey of NonStop from where it is today to a virtualized NonStop in the future.
Andrew’s key messages were:
· There is a mission critical renaissance
· Digital core is critical to business transformation
· HPE is committed to NonStop innovation
Andrew also gave a glimpse of what lies ahead for NonStop long-term based on NonStop X, virtualized NonStop and Database services. Things like specific Telco offerings, Utility markets, Internet of Things and even Blockchain are all application areas where the NonStop fundamentals could play a significant part.
Dave McLeod, Director HPE NED EMEA, happily reported that the first 6 months of the fiscal year have been very good indeed and his team was able to overachieve on its targets. HPE continuous to roll out the NS X systems and is reaching a tipping point where NS X approaches 50% of the NonStop business (in EMEA). Dave remains optimistic about the rest of the year and presented the future platform choices for customers
1) converged NS X systems
2) virtualized NonStop
3) a combination of the two.
Most demand for virtualized NonStop is to come from the Telco space followed by Financial Services albeit mainly on test and development systems. He reminded everyone of HPE NonStop’s track record of the past years in announcing and delivering NS X, Yuma and vNS. The future of vNS will see new database capabilities supporting the digital core concept that Andrew spoke about in his presentation.
From comForte’s point of view and being one of the sponsors of the event, it was a great couple of days and we surely managed to make an impression with the James Bond theme.
Read the whole story here
TANGO’S NATIVE ANTI-FRAUD FEATURES REPORT
Lusis has led several research projects with Universities and research
institutes in the anti-fraud space. This research activity has enabled
Lusis to build both a consulting practice and a library of conceptual
tools and software modules than can be used in specific projects. Lusis’
TANGO solution embeds an anti-fraud service that has been successfully
implemented by several large French banks for many years. This service
can be provided as an independent TANGO environment application.
List of features:
-
The capacity to
integrate flows from various sources: (ISO 8583 messages, JSON Rest
API, XLM, WEB services, Files, ISO 20022 messaging) and interconnect
to switches using API, ISO 8583 messages, WEB services, JSON Rest
API
-
A powerful rule
based Boolean language and real time engine allowing Markovian
antifraud processing
-
A complementary
authorization engine allowing non-Markovian antifraud processing
-
A GUI to set up
rules and monitor alerts
Read the
complete report HERE.
For more
information about TANGO contact Brian Miller at
brian.miller@lusispayments.com or
visit
http://www.lusispayments.com
Brian
Miller
Lusis Payments, North America
(415)
829-4577
Brian.Miller@lusispayments.com
XYPRO Team Profiles: Support Guru Leads Layer8 to CCDC Nationals
As XYPRO continues to grow as a company, so does the team of outstanding individuals that support us. For many members of our team security is much more than a job, it is a passion. Sepand Hormozdiary of the XYPRO support team is no exception. Sepand has been around computers his entire life and this year he was chosen to be the captain of his team, Layer8, in one of the nation’s most prestigious cybersecurity competitions, the National Collegiate Cyber Defense Competition (CCDC). After the competition I was able to chat with Sepand about his experience.
Sepand Hormozdiary

Hey Sepand, tell everyone a little bit about yourself:
I am a senior at California State University Northridge (CSUN), majoring in computer information technology. I am part of the XYPRO Technical Customer Support department, where I started as an intern before being offered a permanent position. I graduate from CSUN in May, 2017.
Computer technology has always been my passion and I have been working in this field more than a decade. I returned to school because I felt the need to an academic degree to complement my professional experience.
 Why
are you passionate about your major?
Why
are you passionate about your major?
My father introduced me to my first consumer computer the “Commodore 64” at a very young age and I felt this is something that I can do for the rest of my life. Later, I was introduced to Windows NT 4.0 and networking.
Eventually, I obtained my CCNA and MCP degree while I was working in one of the largest petrochemical companies in the middle-east.
What is Layer 8?

CSUN’s Layer8 Computer Security Club is an educational student club that focuses on cyber security at different levels. They work on various security projects during the semester that include lectures on how to attack physical locks or lock picking, decompiling programs, reverse engineering, pen testing Wi-Fi, and ethical hacking.
Club members participate in different online cybersecurity competitions such as CTF (Capture the Flag) and qualified members eventually become part of the WRCCDC (Western Regional Collegiate Cyber Defense Competition).
Why are you involved?
I love the challenge and I am also nominated by the Layer 8 Club board to serve as the team leader due to my 10+ years of experience in Network engineering and System Administration in the telecom and oil industries.
What is the CCDC (Collegiate Cyber Defense Competition)?
The CCDC is a competition between a Blue Team (Service Providers) and a Red Team (Professional Pen Tester). The blue teams have to respond to administrative tasks that are dictated by a fictitious company. The blue team also has to respond to threats coming from live opponents (Red Team).
The 2017 Western Regional Collegiate Cyber Defense Competition (WRCCDC) was won by the CSUN Layer8 (blue) team against very tough competition that included Stanford University, University of California, Berkeley, Cal Poly Pomona, University of California, Riverside, Arizona State University, California State University, San Bernardino and University of Advancing Technology.
More about the competition from the WRCCDC website:
“CCDC competitions ask student teams to assume administrative and protective duties for an existing “commercial” network – typically a small company with 50+ users, 7 to 10 servers, and common Internet services such as a web server, a mail server, and an e-commerce site. Each team begins the competition with an identical set of hardware and software for their fictitious business and teams are scored on their ability to detect and respond to outside threats, maintain availability of existing services such as mail servers and web servers, respond to business requests such as the addition or removal of additional services, and balance security needs against business needs. Throughout the competition, an automated scoring engine is used to verify the functionality and availability of each team’s services on a periodic basis while traffic generators continuously feed simulated user traffic into the competition network. A volunteer red team provides the “external threat” that all Internet-based services face and allows the teams to match their defensive skills against live opponents.”
Why does Layer 8 participate in CCDC?
Layer 8 is a student club focused on cyber security and IT. To fill the gap between academia and real world challenges, Layer 8 is focusing on the areas that academia does not provide enough coverage due to legal or other resource limitations. CCDC is the best way to put the material students practiced in the Layer 8 lab into an action.
Who is on the team?

Each school can send a list of 12 students to WRCCDC and 8 students can play in the competition. Since competition is covering a different area of cyber security, each team consist of 3 specialized teams (Windows, Linux, and Networking) and one person to accept\submit business inquiries submitted from a fictitious company.
CSUN’s reputation at the event
In the past, the team reached as high as 3rd place, but in WRCCDC 2017 for the first time, CSUN Layer8 placed first.

A word from Sepand’s Manager, Robert Massa
It’s a pleasure to work with Sepand and utilize his security skills to help solve technical customer issues reported by customers, as well as internal corporate security concerns. He is an enthusiastic individual who works relentlessly to find answers to the often complex support issues that he has to deal with on a daily basis.
XYPRO is a proud sponsor of CSUN’s Layer8 Computer Security Club and congratulates the team on their achievements.
Casey Krasner
Marketing Coordinator
comForte eBITUG Video - Keeping your data 'For yo#2 636& only’ Part I
In case you missed it: The link below you will take you the first part of John Bycrofts presentation "Keeping your data 'For yo#2 636& only’" that he gave at eBITUG in London.
Follow the link: https://comforte.com/ebitug/
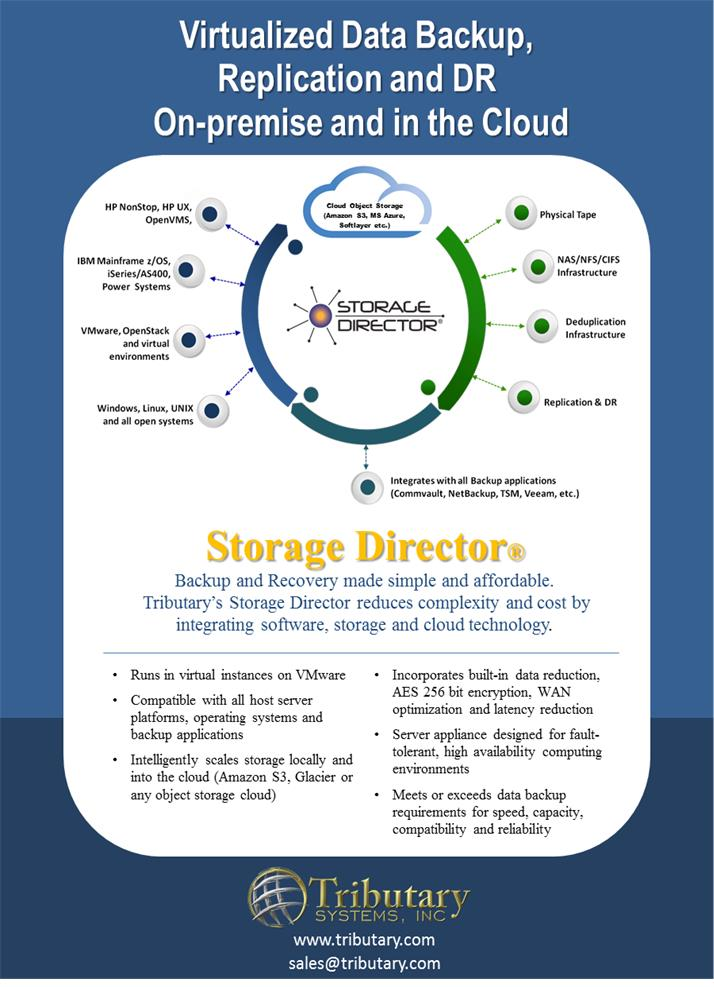
Smashing Silos- Tributary Systems Storage Director and Cloud Object Storage
By Glenn Garrahan, Director HPE Business, Tributary Systems
What’s Object Storage?
Object Storage architecture manages data as objects, unlike file systems which manage data as a file hierarchy or block storage which manages data as blocks within sectors and tracks. Each object will include the data itself, some amount of
metadata, and a globally unique identifier. Object storage can be implemented at multiple levels, including the object storage device level, the system level, and/or the interface level. The advantage of object storage is it enables capabilities not addressed by older storage architectures. Examples may include interfaces that are directly programmable by the application, a namespace that can span multiple instances of physical hardware, and data management functions like data replication and data distribution at object-level granularity.Massive amounts of unstructured data may be retained efficiently by object storage. Object storage is ideal for purposes such as archiving photos, songs, videos, etc.
The Future of Archiving- Object Storage
There’s no doubt, the future of archiving is object storage. It is lower cost, flexible and highly scalable. Object storage will replace dedup disk technology as an archival methodology. Billed as a replacement for tape archival, dedup was somewhat attractive back in 2007 when disk costs were higher. Even then, however, it was not as low cost as tape on a per megabyte basis.
Fast forward to 2017, now with much lower cost, higher capacity disk, dedup is slow, cumbersome, and very expensive plus it scales poorly.
There are many great reasons why Amazon S3, Google cloud, MS Azure and all other public clouds use object storage. Its flexibility, scalability, and cost are all substantive advantages customers realize when retaining huge amounts of unstructured data in the cloud. Object storage (outside of back up and archive) can also be flexible with users being able to access data from anywhere.
IBM's Cloud Object Storage (ICOS) has an industry leading, low cost, highly secure (impossible to hack - yes impossible because of its erasure coding technology) and highly scalable architecture. ICOS can be implemented on premise if a customer wants it and has a data backup/archive footprint larger than 500TB. It can be consumed on the IBM Cloud (called Bluemix) just like Amazon or Azure at any size backup footprint.
TSI’s Value Proposition
How will a NonStop customer take advantage of cloud object storage in general, and ICOS specifically? With Storage Director of course!
First, Storage Director is the only way to backup HPE NonStop, iSeries, and/or Mainframe data to any object storage (S3 interface) as it has a FC front end and a FC, NAS (NFS) or S3 backend.
Secondly, any backup application directly connected to ICOS is slow due to the methodology by which ICOS ingests data and applies erasure coding (also called dispersed storage algorithm). But Storage Director is superfast ingesting data from any backup application including NonStop, TSM, Commvault, NetBackup, Veeam etc.; so installation of a Storage Director appliance between your NonStop host and ICOS will allow rapid data ingestion and caching to reduce backup windows while streaming the data policy based pools to ICOS at the back end. Archiving post process to the backup constitutes a strong value proposition for NonStop customers employing IBM ICOS.
In addition to Cloud Object Storage connectivity, there are other important features that Storage Director brings to the HPE NonStop environment, including:
1. Storage Director facilitates clustering to allow the handling of large quantities of data via clustered nodes, ensuring adequate connectivity for both data sources and converged data storage infrastructure while streamlining the management of both the Storage Director appliance and the tiered policies it implements.
2.
Storage Director natively connects to all servers and storage in the enterprise, with no middleware or agents or third party software. This is a key; Storage Director is capable of being dropped into any complex of servers and storage devices, supports all connectivity protocols, minimizing disruptions and simplifying implementation.
3. Being policy-based, Storage Director enables NonStop users to place data from different applications and host servers into data pools with different retention, location and replication policies. This means that data can be retained in the most cost effective manner. TSI’s Storage Director is storage device or location “agnostic”.
4. Secure vaulting (employing built-in encryption) of data to any cloud object storage is crucial. The Storage Director tiered policy-based device allows customers to vault appropriate data to the cloud for a second copy or disaster recovery while sending other, perhaps more essential, data to local disk or tape, all concurrently, all securely, with replication rates that meet the requirements of the enterprise.
5. TSI’s Storage Director is specifically designed for fault-tolerant, high availability NonStop computing environments, given the centralized location of such a device in the data stream.
With Storage Director, enterprises can tier stored data and data policies down to individual data volumes on multiple host platforms based on business criteria and importance to business resiliency and restoration. This is intelligent data management!
In enterprises with multiple host platforms – HPE NonStop NB, NS and now NonStop X servers, HPE Open VMS, Windows and VMware running HPE Data Protector, IBM zOS mainframes, IBM AS/400s iOS (now IBM PowerSystems), among others – Storage Director enables sharing storage technologies otherwise dedicated to each host platform. Such a converged approach improves storage performance, enables consolidation, and can lead to measureable savings on a “per TB” of retained data.
XYPRO looks forward to seeing you at the upcoming shows!
NYTUG – 2017May 25, 2017Event Website >
N2TUG – 2017June 1, 2017Grapevine, TexasEvent Website >
ACI User Group Exchange – 2017June 26, 2017 June 29, 2017JW Marriott Desert Ridge Resort and Spa in Phoenix, Arizona, U.S.Event Website >
ATUG 2017September 20, 2017Atlanta, Ga, Home Depot HQEvent Website >
CTUG – 2017October 11, 2017 October 12, 2017HPE Canada Headquarters 5150 Spectrum Way , MississaugaEvent Website >
NonStop Technical Boot Camp – 2017November 13, 2017 November 15, 2017San Jose, Ca.Event Website >
CSP Steals the Show at eBITUG in London!

eBITUG Dates: May 9-10, 2017
Event Location: aqua shard, The Shard, 31 Saint Thomas Street, London, UK.
On the evening of May 9th, EBITUG attendees were invited to an extraordinary event presented by CSP, Evening at aqua shard. This unforgettable event was held at the glamorous aqua shard restaurant, located on the 31st floor of The Shard – the tallest building in Western Europe. Guests experienced spectacular panoramic views of London from a 930 sq m dining room and triple height atrium bar located in this world-renowned building.




Approximately 250 guests were greeted with a Champagne reception followed by complimentary drinks and a selection of elegant contemporary British canapés and bowl food from the Executive Chef. In addition, those in attendance were treated to an incredible live performance by the Andy James Band in the 200-capacity Gin Wing space of aqua shard. We would like to thank everyone who joined us and hope you had a memorable evening.
Some of the many comments from our guests:
"We just wanted to thank you again for the amazing and fun experience we had at the Aqua Shard event that you and your team hosted. By all accounts, it was a blast and we really appreciate being invited. As a vendor, we often don’t get to participate in such wonderful venues that are being hosted by another vendor, and I think that also made it really special for us and the others."
"Thank you also for the party at Aqua Shard. The place, the band and the views were really unforgettable!"
"Folks who attended the event and your evening at the Shard said it was the highlight of the show"
"This was a super "millennium" Event and every time the TUGs will sit together - it will be talked about Aqua Shard"
"You have sponsored and hosted a truly high class and certainly unforgettable event at the shard last Tue - I have generally heard overwhelming feedback and can only underline this with big compliments from our side"

The following day, CTO, Callum Barclay presented "Security for the Brave New World" at one of the conference’s plenary sessions. In his well attended presentation, Callum discussed Protect-X, CSP’s revolutionary browser-based product built to address the fundamental security challenges faced by mixed-platform environments, including Virtual NonStop. Callum also discussed how a layered approach can reduce the opportunity for hacker attacks.
CSP’s President & CEO, Vernette O’Neill, CTO, Callum Barclay and members of the CSP team were pleased to attend and sponsor the 2017 EBITUG conference. We would like to thank the EBITUG committee and volunteers for organizing the conference as well as all the attendees for making EBITUG 2017 a resounding success.
For more information on CSP solutions visit www.cspsecurity.com
For complimentary access to CSP-Wiki®, an extensive repository of NonStop security knowledge and best practices, please visit wiki.cspsecurity.com
We Built the Wiki for NonStop Security
TM.Regards,
The CSP Team
+1(905) 568 - 8900
Ask TandemWorld
Got a question about NonStop ? ASK Tandemworld
Keep up with us on Twitter @tandemworld
comForte - eBook on Modernizing Applications on the NonStop Platform

Why should you modernize your proven applications, what are the best strategies to do so and which areas should be addressed when modernizing legacy applications?
Nowadays, new and rapidly evolving enterprise IT platforms, delivery models, and capabilities provide an opportunity to increase users, innovate delivery, and extend the business value of technology across the enterprise. But to do so, IT departments must adapt, which often entails transforming proven applications to take advantage of emerging technologies.
Download the eBook
“Event-full” times for DataExpress
We would have liked to catch up with Jimmy Treybig, as so many of you
apparently did during the recent eBITUG event in London. Even though our
offices are here in Dallas and Jimmy spends most of his time a little
south of us in Austin our paths rarely cross these days. Jimmy fathered
Tandem Computers and the changes that the introduction of fault tolerant
computers brought about in the industry remain hard to ignore. While we
didn’t manage to find our way to London, we will definitely be in Dallas
for the upcoming N2TUG event, June 1st.
Here at DataExpress there continues to be conversations among the team
following what we heard at the recent NonStop Partner Symposium. We left
that event aware that the models we have held onto for a very long time
need to be updated. While NonStop X is just another refresh of the
hardware, albeit this time with greater emphasis on industry standards
and openness, the news that there will be a Virtualized NonStop (vNS) is
resonating in ways that has aroused our curiosity about who exactly will
be opting for a NonStop running in a virtual machine instead of in a
physical machine. It is still very early days, with NonStop product
management carefully overseeing who exactly gets vNS, but we expect to
run into early deployments at some point.
For the time being, NonStop X systems remain our focus as we are seeing
that our customers now have concrete plans in place for upgrading to
NonStop X. Customer requirements continue to be generated and there are
changes taking place within the DataExpress NonStop (DXNS) code, and
even though these latest updates to DXNS are small, we find ourselves
back in testing mode for NonStop X. As a NonStop vendor we have to agree
with all those making similar observations – NonStop X performs much
better than any predecessor NonStop system and we are watching to see
whether our users elect to deploy more applications on NonStop than they
otherwise might have thought of doing in the past.
We have seen our customers now with multiple instances of DXNS running
and even though this is a capability that has been supported by us for
some time, it has led to us working on a “single-view” interface on the
NonStop allowing customers running multiple instances of DXNS to view
them from a single pane of glass – just one console display to see all
that is happening across these multiple instances of DXNS. We are doing
this now in response to our own observations of what customers have been
doing and with the deployment of NonStop X our expectation is that there
will be more customers who elect to run even more instances of DXNS than
in the past.
“As word gets around the NonStop community that we can make the process
of moving files a lot easier and that the automation we bring to the
table eases the pain that is otherwise generated when things go wrong,”
said DataExpress President, Michelle Marost, “we are anticipating more
interest in our solution.” DataExpress has been a quietly kept secret
for several decades now but word is getting out there about what we can
do and the benefits that come with a solution that is independent of the
actual file transfer product being used, even as DataExpress has the
unique ability to oversee multiple file transfer products. “A business
may elect to rely on just one file transfer product but in today’s
highly networked world where customer and business partners are
connected, the likelihood of having just one file transfer product
deployed by everyone in the network is highly unlikely. Customers really
do need DataExpress to reduce the complexities that can arise where
there are multiple products deployed.”
The participation by NonStop users in events wherever they are held
around the world is an encouraging sign for all vendors. A full calendar
of events reflects a real interest in all things NonStop and this we
find not just encouraging but challenging as well. Diversification is
certainly going to happen as we see NonStop running on virtual and
physical systems and how customers embrace one or the other or perhaps
both will have a big impact on future features of DataExpress.
Like everyone in the industry today we are watching the deployment of
cloud computing among our customers even as we watch take-up of hybrid
IT. Having a presence at some of the biggest NonStop users in North
America means that we will get to see a variety of deployments as they
push to run NonStop in ways we hadn’t conceived of just a few years ago.
These customers will allow us to track where NonStop will likely head
and we have to believe that at upcoming events between now and the 2017
NonStop Technical Boot Camp we will hear even more about the future
deployment plans for NonStop from these very big users of NonStop.
We have written about this before but the future deployment plans for
DataExpress will likely lead us to where DataExpress will be available
on the basis of Software as a Service, something we are open to discuss
further with our NonStop users. And of course, when that happens you
will hear about it at an event being held somewhere near you. Of course,
if you can’t wait to hear more about this, then call us or drop us an
email – we would be only too happy to schedule a call and a
demonstration for you at your convenience.
sales@dataexpress.com | +1.972.899.3476
https://www.dataexpress.com
comForte events near you:
Meet the comForte team on the following NonStop events
|
Events |
Date & Location |
|
NYTUG |
May 25, 2017 – Berkeley, NJ, USA |
|
N2TUG |
June 1st, 2017 - Grapevine, TX, USA |
|
ATUG |
September 20, 2017 - Atlanta, GA, USA |
|
Technical Boot Camp |
November 12-15, 2017 - San Jose, CA, USA |
Registration for the
2017 NonStop Technical Boot Camp is OPEN!
Connect Worldwide invites you to join
the NonStop community at the 2017 NonStop Technical Boot Camp at the
Hyatt Regency San Francisco Airport in Burlingame, California on November
12-15, 2017.
We encourage you to take advantage of the EARLY
BIRD registration rate of
$1295 until September 1st!
Learn More and Register Now!
Connect is at the forefront of today's
open system leaders and is a true user-driven consortium of HPE
customers and partners working with HPE's NonStop Enterprise Division.
The 2017 NonStop Technical Boot Camp will begin with cutting edge
deep-dive pre-conference seminars on
Sunday hosted by the leaders of NonStop innovations and solutions and
will follow with three days of breakout
sessions, keynotes, and networking receptions. Meet and learn
from the developers, engineers, and executives that are leading the
global NonStop community. Click
here to get started.
Reserve Your Room at the Hyatt Regency SFO
Today.
Connect has secured a great room rate
for Boot Campers at the
Hyatt Regency San Francisco Airport.
Reserve your room before October 20,
2017 to get the Group Rate of
$235 per night. To reserve
your room online now,
click here.
Call for Papers is OPEN!
Do you have an interesting NonStop topic
that you would like to present at this year's Boot Camp?
Learn more and submit your
paper here. The Call for
Papers closes on September 1st.
No matter if you are new to NonStop or have years of experience, there
is something at Boot Camp for you. Click
here to learn more and get
registered today.
See you at Boot Camp!
~ Connect Events Team
Find out more about us at
www.tandemworld.net
+44 (0) 20 8304 7979
We would like to thank the sponsors of the May 2017 eNewsletter
Platinum Sponsor is
Gold Sponsor
Silver Sponsor
To enquire about Sponsorship opportunities for the Tandemworld Newsletter please click here.
Current Subscribers 15127
Our company, Tandemworld, accepts no
liability for the content of this email, or for the consequences of any
actions taken on the basis of the information provided.
To Unsubscribe or Change your Subscription Please click here



