
Tandemworld eNewsletter for September 2016
Platinum Sponsor is
Gold Sponsor
Silver Sponsor
Tandemworld eNewsletter for September 2016
Contents
comForte - Events near you
comForte - With Yuma, NonStop X Has Become a Full Software Solution
XYPRO looks forward to seeing you throughout 2016
comForte - Webinar: Modernizing Payment Applications on the NonStop Platform: Hype or Hope?
XYPRO is proud to be a Diamond Sponsor for this year’s NonStop Technical Boot Camp!
comForte - Technical Boot Camp website
Musings on NonStop! - September, ‘16
for 20 years without fail
Current Subscribers 15102
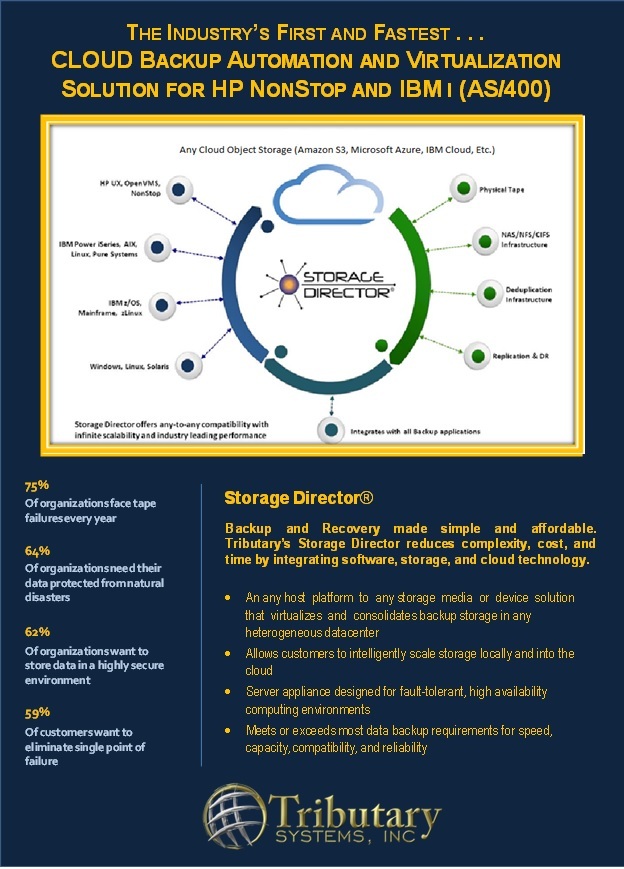
Tributary Systems’ Storage Director 5.0: Policy Based Data Management for the NonStop Professional
By Glenn Garrahan, Director of HP Business for Tributary Systems
Policy Based Data Management- sounds impressive, but what does
it really mean and how does the NonStop professional benefit by its
implementation?
Every enterprise has at least one location where the bulk of the
corporate data resides. This could be a tape physical tape library, a
virtual tape server, a VTL, whatever. Now wouldn’t it be sensible to
make this data location a “storage services director,” where data
protection, data management and archiving services could be applied to
all data assets per customer derived, pre-established, policies. By
creating these data management policies, pools of data can be managed
based on considerations such as protection and recovery requirements,
the diversity of threats to the data, and storage cost. Backing up
mission critical data to tape might well exceed data restore SLA’s, long
term archiving of low priority data on expensive SDD’s may be overkill
and a waste of resources.
A federated approach, in which a “storage director” serves as the
cornerstone of policy-based data management services delivery, is
quickly gaining mindshare among NonStop users. Storage directors must
facilitate the handling of large quantities of data; ensure adequate
connectivity for both data sources, converged data storage
infrastructure and streamline the management of the policies customers
implement.
There is only one company that has taken this approach for the HPE
NonStop professional, Tributary Systems; whose Storage Director® 5.0
product is a customer centric software defined policy-based data
management solution that connects “any host to any storage technology”.
Storage Director applies appropriate protective, management and archival
services to data, while simultaneously converging the backup
infrastructure. In fact, Tributary Systems is an HPE Converged
Infrastructure Ready Solutions Partner.
With Tributary Systems' Storage Director, enterprises can apply data
policies down to individual data volumes on host platforms (such as HPE
NonStop), based on business criteria and importance to business
resiliency and restoration. This is intelligent data management!
In enterprises with multiple host platforms – HPE NonStop NB, NS and now
NonStop X servers, Superdome X servers, HPE Open VMS, Windows and VMware
running HPE Data Protector, IBM zOS mainframes, IBM AS/400s iOS (now IBM
PowerSystems), among others – Storage Director enables sharing storage
technologies otherwise dedicated to each host platform. Such storage
technologies can include existing enterprise storage disk, HPE StoreOnce,
EMC Data Domain, and Quantum DXI data de-duplication devices, physical
tape, Amazon S3, Microsoft Azure and Openstack compatible Cloud, or any
combination of storage technologies dictated by customer data management
needs. Such a converged approach improves storage performance, enables
consolidation, and can lead to real savings of time, power and most
importantly staff.
Storage Director 5.0 offers numerous compelling features for NonStop
professionals:
Storage Director 5.0 virtualizes and consolidates data backup to a
single storage target in any heterogeneous datacenter-
• The product is designed for high availability computing environments
and meets or exceeds data backup requirements for speed, capacity,
compatibility and reliability
• Storage Director has full tape library management capabilities,
allowing not only tape drive but also back-end physical tape library
connection, including all HPE NonStop LTO Tape devices
• Storage Director has tape stacking, caching, data management,
replication, monitoring and alerting capabilities; it also has the
capability to be a transparent pass-through device
• Storage Director provides seamless integration of disk, tape and fully
supports HPE StoreOnce, EMC Data Domain and Quantum DXI de-duplication
technologies; Storage Director is an officially certified and supported
solution by EMC, HPE Storage, and Quantum in HPE NonStop environments
• Storage Director utilizes AES 256 bit encryption
• Storage Director supports LZ compression in cache
• The product is non-disruptive to existing backup environments and
NonStop applications, and enables NonStop data migration to Amazon S3,
Microsoft Azure and Openstack compatible Clouds
• Storage Director fully supports NonStop data format
• Supports iSCSI or Fiber Channel attachment to storage devices
• Supports NonStop host IOAME/VIO/CLIM FC attachment
• Fully tested with HPE StoreOnce, EMC Data Domain and Quantum DXI
de-duplication storage devices
• Storage Director has an intuitive easy to use GUI
Another important capability Storage Director provides is the ability to
meet physical tape, de-duplication and remote site replication. This is
a fully tested configuration which allows NonStop professionals to use
the replication features inherent in data backup systems.
Scalable and Expandable
As backup requirements change, so too can Storage Director. Additional
virtual libraries, drives, and tapes are easily added through a
web-based GUI. Additional disk cache enclosures can be introduced into
the system and throughput performance and higher availability can be
achieved through the multi-node architecture. Storage Director will meet
the needs of today and protect your investment by meeting a different
set of needs tomorrow.
Contact Information
ggarrahan@tributary.com or visit our website: www.tributary.com
Tributary Systems, Inc. is a technology solution provider to enterprise
computing customers. Tributary develops and sells data protection,
backup storage, virtualization, site-to-site replication and disaster
recovery solutions. Tributary is an acknowledged global leader in
providing backup storage and data protection solutions for
fault-tolerant, high availability, enterprise computing environments.
Tributary was founded in 1990 and is a Texas based company with its
headquarters, development, integration, and test facilities in Bedford,
Texas.
Through its channels and direct sales organization, Tributary has served
customers worldwide, predominantly in the banking, financial services,
retail, telecom and healthcare industries. Tributary is a HPE business
partner and OEM supplier, IBM OEM Partner (iOEM), Solution Reseller (ISR)
and Business Partner, Quantum® Value-Added Reseller (VAR), and Oracle®
OEM partner.
Be sure to visit us in the Tributary Systems’ Booth at the 2016 NonStop
Bootcamp this November!
Worried About a Fuzzy View of Your Data?
Shadowbase Online Loader, SOLV, Will Clear Your Vision
Traditional target database loading gives you a “fuzzy” view of your data for an extended time. The ETL loaded data represents a snapshot of the past, and is old and stale until replication refreshes the offline loaded target data from the replication queue files. For a large database, this replication could take days or weeks to resolve, a time during which your target data is fuzzy and incomplete.
Instead, Gravic provides a patented online loader called SOLV which clears your vision. Replication and target database loading happen at the same time and are coordinated so that the data in the target database is current and matches the source database. Double vision is gone and your data is available without a big-bang cutover, which could be a thud.
SOLV is a unique capability only available to HPE Shadowbase users. For more information on SOLV, please contact your local HPE account team or visit our website. To speak with us about SOLV or your data replication and data integration needs, please visit us at www.ShadowbaseSoftware.com, email us at SBProductManagement@gravic.com, or call us at +1.610.647.6250. Hewlett Packard Enterprise directly sells and supports Shadowbase Solutions under the name HPE Shadowbase
Gravic Presents on HPE Shadowbase Zero Downtime Migration Technology at
VNUG Conference
This month, Gravic attended the VNUG Nordic Users Conference at the beautiful Ranas Slott Castle outside of Stockholm, Sweden, and presented on Improving Uptime and Eliminating Risk for Disruptive Migrations with HPE Shadowbase Zero Downtime Migration (ZDM) Technology. VNUG is a special event, engaging customers with great content and HPE and vendor support, while providing many networking opportunities. Congratulations to Thomas Monell of Evry Card for winning our GoPro Hero camera!
Gravic Presents at First-Ever Greater New York/New Jersey Area
HPE & Partner NonStop Information Day
Last week, Gravic presented at the first-ever Greater New York/New Jersey Area HPE & Partner NonStop Information Day, held for partners and users at the HPE Offices in Berkeley Heights, NJ. Our presentation on Shadowbase ZDM demonstrated how customers are leveraging HPE Shadowbase solutions to perform zero downtime migrations, and to safely eliminate planned downtime with no loss of business services for otherwise risky and disruptive application, database, and operating system upgrades. Several use case scenarios were reviewed for both homogeneous and heterogeneous migrations. If you are interested in discussing this presentation’s content or would like us to present this or other HPE Shadowbase topics to your staff, please
contact us.
Please Visit Gravic at these Upcoming 2016 Events
|
ATUG Meeting—Atlanta, 29 Sept. |
|
|
|
CTUG Conference—Toronto, 19 Oct. |
|
|
|
NENUG Meeting—Andover, MA, 20 Oct. |
|
|
|
Connect NonStop TBC—San Jose, CA, 13-16 Nov. |
|
|
Please Visit Gravic at these Sites
|
Gravic Website http://www.shadowbasesoftware.com |
|
|
|
HPE Website http://www.hp.com/go/nonstopcontinuity |
|
|
|
Twitter https://twitter.com/GravicSB |
|
|
|
|
|
|
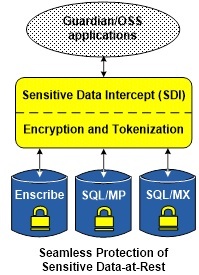
TANDsoft’s Sensitive Data Intercept (SDI) Protects Sensitive Data-at-Rest for Enscribe, SQL/MP, and SQL/MX
TANDsoft Inc. wants your
data to be completely useless to hackers. Worthless, unprofitable,
totally meaningless. For this purpose, TANDsoft is collaborating with
HPE NonStop security partners to protect your sensitive data-at-rest via
its SDI solution for Enscribe, SQL/MP, and SQL/MX databases.
SDI stands for Sensitive Data Intercept. It intercepts HPE NonStop
database access calls, then encrypts / tokenizes data written to disk
and decrypts / de-tokenizes data read from disk. TANDsoft’s years of
expertise in interception technology makes it all happen without the
need for any application modifications, of particular importance when
the source code is unavailable.
Now embedded into the solutions of major HPE NonStop security partners,
SDI is in trial with several customers. For users of HPE SecureData, SDI
provides additional encryption and tokenization capabilities.
SDI Features and Benefits
• Available on all HPE NonStop servers
• Supports NonStop Enscribe, SQL/MP and SQ/MX
• Supports native and non-native applications
• No application modifications required
• Offers additional encryption and tokenization capabilities when
combined with HPE SecureData or NonStop security partner products
• Helps organizations comply with PCI-DSS, IPAA, SOX, and other industry
regulations
• Supports NonStop Guardian and OSS
Interception technology also is the backbone of other TANDsoft
solutions. As is the case with SDI, interception technology allows the
creation of new application functionalities for existing applications
without the need to make source code changes. TANDsoft President Jack Di
Giacomo writes in his article Interception Technology Enhances
Application Functionality, “If you bought software from a third-party
provider, you don’t need the source code. If it’s HPE code, you don’t
need the source code. Even if you wrote the application in-house and
have the source code, you don’t need the source code.” Read the article
at http://bit.ly/Rb8eEM.
In addition to SDI, TANDsoft solutions include FileSync for automatic
file synchronization, replication, and data deduplication; the OPTA2000
virtual clock- and time-zone simulator; the OPTA suite of interception
and trace utilities (OPTA-Trace Online Process Tracer and Analyzer,
Recycle Bin, Low Pin Optimizer, and EMS Alerts Online Startup and
Termination Capture Utility); Stack Monitor, which alerts developers to
the impending threat of a stack overflow; Command Stream Replicator,
which logs and automatically replicates TMF-audited/unaudited FUP,
SQL/MP and SQL/MX DDL structure and other environment changes to target
systems; the Enscribe-2-SQL and TMF-Audit Toolkits and the
Enscribe-2-SQL Data Replicator, all of which offer flexible, affordable
alternatives to more expensive conversion products or manual conversion
techniques; and E2S-Lite, which permits efficient, low-cost Enscribe
modifications without the need to change a program’s source code.
For information about TANDsoft solutions, contact Jack Di Giacomo at +1
(514) 695-2234. Free trials are available. www.tandsoft.com.
Visit TANDsoft at the upcoming Canadian Tandem Users Group (CTUG) event
on 19-20 October in Mississauga, Ontario, Canada. TANDsoft also will
exhibit in the Partner Pavilion at the NonStop Technical Boot Camp,
13-16 November, San Jose, California USA. Visit us in Booth #36.
Integration may be easy but so is support – we have seen it all, rest easy!
Foundations are extremely important for any endeavor, be it the building of a house or skyscraper or a new highway or dock. At the very heart, foundations represent something firm and solid capable of supporting everything that then rises or stretches before us. We don’t have to look very hard or too long before we come to recognize whether a foundation is sound or not and the appearance of cracks and the opening of holes all tell of expediency overriding prudence.Today’s enterprises are fully aware of foundations when it comes to software. They are more likely called infrastructure or low-level code and sometimes even middleware but no matter how you describe it, todays solutions are every bit as dependent on strong foundations as is anything else we build. Good foundations provide flexibility and expand the options available to developers and operators alike – good foundations contribute significantly to any CIO’s peace of mind. Just as with the presence of sound foundations, sound infrastructure is less likely to fail and that too is a message not lost on these CIOs.
In today’s world of constantly evolving technologies and architectures prudent CIOS also look to vendors that provide stability. This is evidenced by blue-chip customers acknowledging a steady stream of new and applicable features, eyes firmly set on tracking these evolving technologies and architectures and support that is 24 X 7, around the clock. With increasing demands coming from legislators and commissions as they watch for privacy breaches, security intrusions and inadequate customer support, as is currently being highlighted in the airline industry with so many failures of its infrastructures of late, more than one Fortune 500 company is basing their advertising on a “steady as you go” mantra.
None of this comes as a surprise to DataExpress. We have provided key infrastructure for several decades and have not just stayed in business through the dot com crises, the fall out following 9 / 11 and more recently, the meltdown that came with the Global Financial Crisis but rather, continued to provide managed and secure file transfer services to some of the biggest of the Global Fortune 1000 companies. File transfer may not be exciting but that is by intent. Ticking over in the background and running neither with fanfare or minute amounts of management attention, DataExpress simply moves the data over and over again.
Visitors to the offices of DataExpress often remark on how serene the office environment looks even as somewhere around the globe multiple files are moving under the oversight of DataExpress. The business of DataExpress revolves around constant testing as we track the many current operating system releases from HPE NonStop and like so many of our compatriots in the NonStop vendor community we too run multiple NonStop systems to ensure compliance with all the latest releases and fixes. And it’s all in the background and without any explanation, completely transparent to any of our visitors.
This is not to say there aren’t customer situations that arise that have all of us at DataExpress working the phones and the systems but there are only a few reasons for such incidents. Something at either endpoint was changed or volumes increased in size unexpectedly or the NonStop system itself was upgraded or there were even configuration changes made to the firewall during a maintenance cycle. One of the obvious downsides from running so unobtrusively is that often times, DataExpress is simply overlooked, essentially, forgotten! As one of our executives put it: “Then ONE transfer at ONE client fails to ONE of their end users, and the phones start ringing!”
By happenstance, routines have been developed within DataExpress to manage such crisis and for the most part, our prudence in being prepared doesn’t go unnoticed. There is the almost instantaneous exchange of trace files, log files, conference calls, demands on how long it will take to fix (in most circumstances, the problem has not even been identified yet), confirmation from DataExpress we will work through the night / weekend etc. Not to mention that oft-requested “can you get your team onto our site?” But our foundations are strong and as yet, together with our customers, we have seen no evidence of cracks or holes in what is for those running DataExpress a crucial foundation for much of what they must do on a daily basis.
For many NonStop users DataExpress is the foundation for core infrastructure around which these NonStop users have built additional application suites that in some cases has led to the development of new business opportunities with sizable revenue-creation implications. To those businesses that just don’t have the resources to respond to the many legislative and commission mandates, for a fee an enterprise with the processes in place can on-sell their established services and this is something we are really thrilled to see happening. DataExpress as a source of new revenues that in most cases more than offset our fees is pleasing to see!
Of course, like many other NonStop vendors we are keeping our eye on the growth in the NonStop X business together with the stated objective of HPE to transform to a hybrid infrastructure made up of traditional IT and private clouds. There is certainly market appeal for both of these – NonStop X with its better price performance metrics and the hybrid infrastructure making it easy to push some processes to Linux and Windows and even private clouds. And after a fashion, treating NonStop with an attached Linux or Windows is the type of baby-step approach we see prudent CIOs evaluating and with both DataExpress NonStop (DXNS) and Data Express Open Platform (DXOP) we are well positioned no matter the direction taken by these CIOs.
Foundations are increasingly important and building next generation solutions on solid foundations is a must for all CIOs. Even for the NonStop community, the changes influenced by cloud computing are inescapable but we can see clearly the steps that need to be taken and for DataExpress, it will be all about the experiences and knowledge we have with running DataExpress on different runtime platforms. It may not be a case of returning to the lazy days of summer, quietly sitting in a beach chair somewhere watching the tide slowly advancing up the beach – but we are prepared all the same. Yes, our foundations are rock solid and this is not lost on any of the prudent CIOs with whom we work today.
DataExpress, Inc.
1401 Shoal Creek, Suite 250, Highland Village, TX 75077
972-899-3476 (sales)
972-899-3460 (corporate)
sales@dataexpress.com
www.dataexpress.com
Secure, Fraud-Resistant, NonStop Banking-on-the-Go
from OmniPayments
The OmniPayments Mobile Banking App brings real-time, anywhere banking and financial-transaction convenience to your customers via their digital devices. It is intuitive, user-friendly, and highly secure and is architected for the Android operating system. Built on OmniPayments’ fault-tolerant HPE NonStop X servers, the App is backed by an automatic failover function to guarantee continuous availability. It readily can be customized to address your unique requirements and those of your customers. We, of course, provide the highest possible security and fraud protection.
OmniPayments Mobile Banking Features
♦♦ Pay bills ♦♦ Transfer funds ♦♦ Recharge prepaid mobile devices ♦♦ Manage loyalty programs & gift cards
♦♦ Make in-store purchases ♦♦ Monitor account & credit/debit card balances ♦♦ Deposit checks
♦♦ Set alerts & reminders ♦♦ Review statements & transactions ♦♦ Access popular, even custom wallets
♦♦ Find ATMs/Branches ♦♦ Block stolen cards ♦♦ Order checks ♦♦ Send feedback ♦♦ ...and more
OmniPayments Mobile Banking Security
♦♦ Sensitive information is masked on screen ♦♦ Four-point logging of each transaction
♦♦ 128-bit or greater encrypted communication between device and host ♦♦ No data is stored on device
♦♦ Potential fraud and compromised accounts can be detected and blocked ♦♦ Logon using unique identifiers
The OmniPayments Financial Ttransaction Switch is a switching solution for the financial and retail industries. It is deployed on NonStop for the highest availability and offers all the requisite functionality to manage credit/debit-card transactions. It manages multiple devices, hosts application interfaces, and interoperates with third-party products or other systems if required. OmniPayments easily expands to provide additional functionality when needed and supplies complete security functions for every financial transaction handled, including encryption-at-rest and encryption-in-flight. Available around the clock, OmniPayments will survive any single fault, requires no downtime for maintenance or upgrades, and supports a range of disaster-recovery solutions.
OmniPayments can be installed either as a complete, off-the-shelf solution or can be enhanced with customer-requested modifications and features to improve cost-effectiveness, efficiency, and risk mitigation. Our team of 100-plus NonStop specialists are skilled at rapid project turnarounds and meeting deadlines.
OmniPayments also distributes OmniCloudX on NonStop X. OmniCloudX hosts numerous OmniPayments instances at a pay-for-use price so attractive that mid-size retailers and financial organizations now can enjoy the benefits of having their own high-capacity transaction switches. Starts at only $5,000 USD per month.
The OmniPayments Preauthorization Engine is used by financial institutions in conjunction with the OmniPayments Financial Transaction Switch or as a seamless interface to other providers’ switches via a custom support module (CSM). We call it the Fraud Blocker!
OmniPayments systems in production today process 700 million transactions per month, generated by point-of-sales terminals and over 14,000 ATMs. A single OmniPayments system supports up to 10,000 transactions per second. Multiple OmniPayments systems can cooperate to provide any capacity required by an application. From our seven worldwide locations, we serve as a 24×7 managed services provider for remote production monitoring.
To learn more about OmniPayments, attend our presentations and visit with our staff at the following events.
ATUG – Atlanta HPE NonStop User Group (29 September) Atlanta, Georgia (USA)
DUST – Desert Users of Tandem (4 October) Scottsdale, Arizona (USA)
PKF – Payments Knowledge Forum (4 October) London, England
CTUG – Canadian Tandem Users Group (19 October) Mississauga, Ontario, Canada
NENUG – New England NonStop User Group (20 October) Andover, Massachusetts (USA)
Nonstop TBC – NonStop Technical Boot Camp (13-16 November) San Jose, California (USA)
OmniPayments customers and others interested in our solutions are invited to join the new OmniPayments Discussion Group on LinkedIn at http://bit.ly/2bB1AGh.
For further information, contact Yash Kapadia at +1 408-446-9274 or at yash@omnipayments.com.
MATUG Fall Meeting Postponed until Late Spring 2017
Due to low attendee registration, and after several discussions with HPE personnel, customers, and other vendors, the MATUG Board has regretfully decided to postpone the MATUG Meeting that was previously scheduled for Tuesday, October 18 at the HPE facilities in Herndon, Virginia. We hope to hold this event in late Spring, 2017, possibly in May or June. We are sorry if this postponement has caused anyone hardship in regards to changing travel plans. We look forward to meeting in the Spring!
Registration Open for NENUG Fall User Meeting
Did you know that you can now register to attend the Northeast NonStop User Group (NENUG) on October 20 in Andover, MA? Registration is open. Don't wait to sign up for this great day of presentations by HPE and its partners!
XYPRO - Breaches are from Mars, Security is from Venus
Be sure to test your security knowledge by taking the short quiz at the end of the article!
There is quite a large disconnect in the way security breaches are evolving versus how security solutions and resources are keeping up to address them, much like the book from John Gray covering relationships and the different motivations, of men and women. Unlike the book though, we’re not trying to come to a happy medium – we’re trying to keep the war like Mars at bay. As a security strategist, I’m constantly evaluating what is possible to help identify gaps and opportunities. The one thing I have learned over the course of my career is:
The only thing constant in cyber security is that attackers’ methods will continue to evolve. They get smarter, more resourceful and are impressively ever patient.
The HPE Integrity NonStop server is not only a foundation of the HPE Server business, it is also central to countless mission-critical environments globally. For the longest time, security of these powerful systems and the “Mission Critical” applications they run remained mostly static and under the radar while high profile attacks on other platforms have taken the spotlight. That hasn’t lessened the risk and exposure of the NonStop server. It’s actually created a gap. With globalization and introduction of new technologies for the NonStop server, this security gap will only increase if not addressed.
Interestingly enough, the NonStop server isn’t the only mission critical enterprise solution in this situation. There are some colorful parallels that can be drawn between applications running on the NonStop server and those running in SAP environments. Both are in highly mission-critical environments and vital to the revenue generation of an organization, and they frequently run payments applications like ACI’s BASE24 and other homegrown applications. This creates some interesting security challenges. In a recent The Connection Magazine Article, Jason Kazarian, Senior Architect at HPE described legacy systems as “complex information systems initially developed well in the past that remain critical to the business in spite of being more difficult or expensive to maintain than modern systems”. His article went on to point out the security challenges of legacy applications. In summary some of these types of applications can tend to be unsupported, security patches aren’t readily available and if they are, they aren’t applied in a timely fashion because of fear of disruption, and they don’t have a lot of the security features modern applications would have. This makes detecting and addressing security risk and anomalies a greater challenge than it already is.
MIND THE GAP
How can this problem be addressed? Protect what you can. As a first step, be it system, application or data – push the risk down the stack to an area that is more controllable by typical security. For example, tokenizing data used by a legacy application will send an attacker to go search for that data through another method, preferably one better suited for detection.
Have a risk based, layered approach. This will swing the odds in your favor. OK, maybe not completely in your favor, but this approach will provide you with the arsenal you previously did not have: It will create those choke points, provide the visibility needed and help reduce mean time to detection and response.
With the way threats are evolving, those of us responsible for security need to constantly evaluate and assess our capabilities. Let’s take a dive into each layer to explore the benefits they provide in an overall security strategy.
Protect
Protection/prevention is the first and most critical layer of any security framework. Without a proper protection layer in place, none of the other layers can be relied upon. Think of the protection layer as the traditional defensive strategy – “the wall built around assets“. This includes defining and implementing a security policy as well as hardening of the network, the system and applications. The protection layer is also where users, roles, access control and audits are set up. Key fundamental concepts to consider as part of the protection layer.
- Authentication – Allows a system to verify that someone is who they claim to be. In a HPE NonStop server environment, this can be done using Safeguard, XYGATE User Authentication, or through application authentication.
- Authorization – Determines what a user can and cannot do on a system. Authorization defines roles and access to resources.
- Access Control – Enforces the required security for a resource or object.
- Logging and Auditing – Ensures that all security events are captured for analysis, reporting and forensics
- Encryption and Tokenization – Secures communication and data both in flight and at rest. Examples of products which protect data include VLE, TLS, SSH, Tokenization and more.
- Vulnerability and Patch Management – Ensure timely installation of all RVUs, SPRs and application updates. Prioritize and take recommended action on HPE Hotstuff notices.
These types of preventative controls are necessary and intended to prevent unauthorized access to resources and data, but they cannot solely be relied on as a long term sustainable security strategy. Attackers’ motivations and sophistication are changing, therefore when prevention fails, detection should kick in while there is still time to respond and prevent damage.
Detect
In testimony given before the Senate Subcommittee on Science, Technology and Space, famed cryptographer and cyber security specialist Bruce Schneier said:
“Prevention systems are never perfect. No bank ever says: “Our safe is so good, we don’t need an alarm system.” No museum ever says: “Our door and window locks are so good, we don’t need night watchmen. Detection and response are how we get security in the real world… “
Schneier gave this testimony back in July of 2001, yet in 2016 where organizations are getting hit by incidents they can’t detect, this premise is still valid and critical. In the previous section we discussed hardening systems and building a wall around assets as the first layer of security strategy. I’m surprised by the number of conversations I have with IT and Security folks who still carry the mindset that this degree of protection and compliance is good enough. No matter what level of protection a system has, given enough time, an attacker will find a way through. The faster you can detect, the faster you can respond, preventing or limiting the amount of damage a security breach can cause.
Detection is not a simple task. The traditional method of detection is through setting up distinct rules or thresholds. For example, if a user fails 3 logons in a span of 5 minutes, detect it and send an alert. In most cases that rule is explicit. If the failed logon events spanned 20 minutes, or worse yet, 10 days, it would not be detected. The limitation with relying on rules for detection is they will not alert on what they don’t know about. Those low and slow incidents and unknown unknowns – activity not normal on a given system -will fly under the radar and no one would be the wiser until you get a call from the FBI.
The other challenge is correlating events from multiple data sources. Let’s look at the incident pattern below.
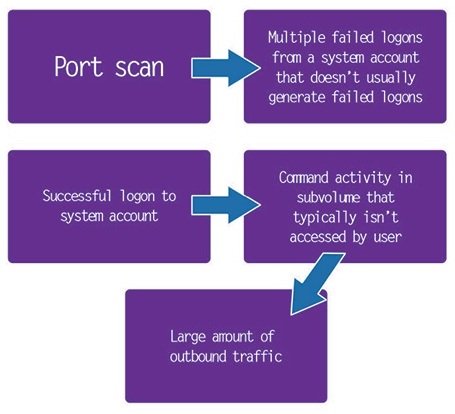
In this incident pattern, we have events from EMS, Safeguard and XYGATE. The NonStop server could send each individual data source to an enterprise SIEM, but the SIEM would not have any context to detect the incident pattern as suspicious behavior. A security analyst could create rules to detect the incident pattern, but that’s just one use case. The traditional method is to scour through event audit records, try to put the pieces together and then create a rule to detect that pattern in the future. The weakness in that thinking is the incident has already occurred. You’re putting a rule together on the off chance it will happen again. However, it’s not reasonable or possible to anticipate and define every possible incident pattern before it happens.
A third area of concern is profiling a system and its behavior to understand what is normal behavior for users, applications and the system to be able to recognize when activity is not normal. This can be accomplished through evaluating the system and its configuration, profiling the system over a period of time, profiling user behavior, highlighting risk management and a variety of other intelligence methods. This is where machine learning has a significant advantage. No human could possibly evaluate the volume of data needed to make these types of determinations at the speed required by today’s standards. Machine learning is a type of artificial intelligence that enables the system to teach itself. Explicit rules are no longer the lone method of detection. Machine learning can profile a system or network over a given amount of time to determine what is normal to isolate what is not normal. Inserting machine learning as part of a solution process significantly increases abilities to stay on top of what is going on with a given system, user, network or enterprise.
Alert
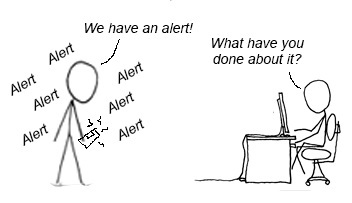
The third layer relies on alerting. The challenge most environments have as they grow and their infrastructure becomes more chaotic with more tools, more users, more data and more events is that they alert too much or too little. How does one know what to act on and what is just noise? There are solutions that position themselves as being able to do data and analytics, but that ends up generating more data from existing data. Now someone needs to determine if the newly formed alert is actionable or just noise.
Going back to our previous failed logon example, if we were to receive 15 different alerts for the same rule, how can one know which alert to pay attention to and which to safely ignore? If you’ve ever been responsible for responding to security alerts, you know this creates alert fatigue. Back in my early days, mass deleting emails of similar types of alerts was one of my favorite things to do.
Contextualization allows the system itself to determine what is actionable and what is just noise. A solution likeXYGATE SecurityOne can evaluate each potential alert and, based on activity that happened previously for that that user, IP, system etc…, determine whether the reported activity is business as usual or a serious issue that needs to be paid attention to. Creating new data and new alerts from existing data doesn’t solve the problem. Applying context to the new incidents generated helps focus efforts on those incidents that truly need attention. Once an account changes hands, it will behave slightly differently.
Contextualization is key.
Respond
For any of the first three layers to produce value, there needs to be a
proper incident response plan.
Responding will allow you to deploy your countermeasures, cut off
access, send the attacker to a mousetrap or other actions that will
assist in minimizing the impacts and recovery of a breach.
Containing the breach and quickly recovering from it are the most important steps of this layer. Response and containment comprise of a number of simultaneous activities to assist in minimizing the impact of a breach. These may include but not limited to:
- Disabling accounts
- Blocking IPs and Ports
- Stopping applications or services
- Changing administrator credentials
- Additional firewalling or null routing
- Isolating systems.
This is necessary to slow down or stop an attack as well as the preservation of evidence. Evidence of the attack is generally gathered from audit logs, but coupled with detection and analytics tools can provide access to information in a much quicker and more granular fashion. Being able to preserve evidence is key is forensic investigations of the breach as well as important for prosecution.
Once all the pieces fall into place and there is an incident alert that requires response, how will your organization deal with the issue? Breach incidents are hardly ever the same. There needs to be a level of categorization and prioritization on how to deal with specific incidents. In some cases, you may want to slowly stalk your attacker, where in others, the sledgehammer approach may be the only thing that can preserve data. Does everyone understand their assigned roles and responsibilities? Is there someone in charge? Is there a documented plan? All of these are considerations that need to be accounted for as part of response. This can be summarized in two words – BE PREPARED.
Resources
On the HPE NonStop server – the protection layer can be addressed with properly configuring Safeguard, implementing protection of data in flight and data at rest and deploying third party security tools available for the system. For alerting and detection, XYGATE Merged Audit with HPE Arcsight can provide the tripwires and alarms necessary for proper detection. For further detail on how to properly protect a NonStop server, HPE has published the HPE NonStop Security Hardening Guide. XYPRO has also published a 10 part blog series on how to properly protect a NonStop server (http://bit.ly/21nmQiY).
For the next generation of detection and alerting, XYPRO’s newest offering, XYGATE SecurityOne (XS1), bringing risk management and visibility into real time. XS1 correlates data from multiple HPE Integrity NonStop server sources, detects anomalies using intelligence and analytics algorithms to recognize event patterns that are deemed out of the ordinary and suspicious for users, the system and environment. Coupled with HPE ArcSight, the solution can provide a constant, real time and intelligent view of actionable data in a way that was never been seen before.
Strong technology and process is important, but people are paramount to any successful security strategy. Constant security training and development on industry best practices, security trends and attack evolution should be factored into any security program. Without ongoing training and reinforcement of people, the gap only has an opportunity to widen. An organizations most valuable resource are the people hired to provide security and close the gap. Use them wisely and ensure they have the tools and training to provide the layers of defense required.
En Finale
Cyber criminals don’t sit around waiting for solutions to catch up. Security complacency ends up being the Achilles Heel of most organizations. Because of its unique attributes, security on the NonStop server needs to be addressed in a layered approach and Risk Management is a big part of the process. Putting the layers in place to allow us to highlight risk as early as possible to address it is key in dealing with upcoming challenges. This will hopefully help bridge the gap between attacks and security.
We need to recognize the paradigm shift and the change in mindset in how we approach security, and attackers’ ability to stay one step ahead of most defenses is central to their strategy. As the NonStop platform evolves and becomes more interconnected, what was put in place previously to address security will not be sustainable going forward. No matter how vendors position their solutions, security is hard, doing the right thing is hard, but that doesn’t mean security professionals need to work harder.
From a security professional’s perspective, cyber criminals will always be viewed as Mars – warlike. Relentlessly driving to break into systems, get to data, wreak havoc and cause disruption to fulfill their malicious objectives. Meanwhile, cyber security staff need to act more like Venus – clouded in mystery and deliberately avoid being seen while following the enemy. If Mars knows our tactics, Mars can avoid them. Mars is at war. Mars is patient. Mars will continue to attack, low and slow. With the proper security layers in place, Mars will be thwarted by deliberate masking, redirection and detection that hides where the data really is and alerts when the enemy is near. We continue to get smarter by blocking, hiding and redirecting things away in response to attacks. But unlike men and women, Venus in the security world has a goal is to keep Mars at bay forever…or longer…
Multi-Factor User Authentication for NonStop
Payment Card Industry Data Security Standard (PCI DSS) v3.2
The latest PCI DSS v3.2 has expanded Requirement 8.3 into sub-requirements, requiring multi-factor authentication for all personnel with non-console administrative access, and all personnel with remote access to the CDE
(cardholder data environment).New Requirement 8.3.1 (effective February 1, 2018) addresses multi-factor authentication for all personnel with non-console administrative access to the CDE.
New Requirement 8.3.2 addresses multi-factor authentication for all personnel with remote access to the CDE (incorporates former Requirement 8.3).
CSP Authenticator
CSP Authenticator provides two-factor authenticated logins to NonStop systems using RSA SecurID Authentication Manager. All communications with the RSA Authentication Manager are fully encrypted.
The Authenticator agent can be configured to include all or some users and terminals. Additionally, selected NonStop users can be assigned to specific RSA ids.
CSP Authenticator can provide authentication services in two ways:
1) Safeguard Authentication SEEP
In this mode, all login attempts by Guardian users that are normally processed against Safeguard are instead passed to the Authenticator agent, which in turn sends the login request to the RSA Authentication Manager for authentication.
2) Pathway Server
In this mode, login attempts through a Pathway application are passed to the Authenticator agent, which in turn sends the login request to the RSA Authentication Manager for authentication.
CSP Authenticator is certified with the latest RSA release and works seamlessly with other security products in the NonStop environment.
For more information please visit www.cspsecurity.com
For complimentary access to CSP-Wiki®, an extensive repository of NonStop security knowledge and best practices, please visit
wiki.cspsecurity.comMeet our team at these upcoming events, as we introduce Protect-X, our new and exciting security solution for hardening SAFEGUARD & OSS:

Regards,
The CSP Team
+1 (905) 568-8900
BITUG NEWS
Coming soon:
·
Autumn Newsletter - will be issued in October 2016 - make sure you register for your copy by joining the BITUG mailing list at www.bitug.com·
Little Sig – Thursday 8th December 2016 at Barclays, Canary Wharf - This event will take the form of an education/training session in the morning from 09:00, user and HPE presentations in the afternoon, BITUG AGM and a social evening.Do Not Miss Out - Mark Your Diary Now – For more info got to:
http://www.bitug.com/little-sig-2016
Registration will open in the next few days.
· The European NonStop Conference and Exhibition and the BIG SIG rolled into one major event (eBITUG):
Do Not Miss Out - Mark Your Diary Now
9th and 10th MAY 2017 at the DoubleTree Hotel – Tower Of London
For the latest information on all BITUG activity and to ensure you are first to know when event registration is open for the above events (there will be limited spaces – so registration will be on a first come, first served basis) please visit http://www.bitug.com and join the BITUG mailing list. Any questions please email chairman@bitug.com
Kevin Poultney
Chairman, BITUG.
BrightStrand International Limited
Visit Lusis at CTUG
If you will be in
Canada October 19-20 for the CTUG
conference, please stop by our booth and get
an on-site presentation of TANGO. TANGO is our
award winning,
mission-critical, transaction processing software solution.
CLICK HERE to
pre-schedule a meeting at
CTUG or one of our upcoming shows.
Here's what others have to say about TANGO:
“TANGO helps us to provide better value, improved transactional performance and reliability.”
- Philip Fayer, CEO, Pivotal Payments
“...TANGO was the best match for our needs and requirements. Lusis Payments has ensured a successful migration, and the solution is now running excellent.”
- Jan Erik Secker, VP, NETS
“Our relationship with Lusis has been a tremendous asset to us. We've worked at all levels together...”
- Randy Meyer, VP Mission Critical Systems, HP
“...not only did TANGO deliver the full capability to replace our existing solution but furthermore it delivered on the promises of flexibility, agility, capability and quality.”
- Pieter Cilliers, CEO, BankservAfrica
Other upcoming events:
NonStop Technical Boot Camp 2016
11/13 - 11/16/2016 Fairmont San Jose Hotel - San Jose, CA, USA
BRIAN MILLER
GENERAL MANAGER
Phone: 415-829-4577
Email: Brian.Miller@lusispayments.com
Website: www. lusispayments.com
Availability Digest Examines HPE’s Software Spinoff to Micro Focus
It is yet another huge HPE announcement in 2016. Earlier this year, HPE merged its Enterprise Services Division with Computer Sciences Corporation (CSC), an arrangement valued at USD $8.5 billion. On 7 September, HPE and global software company Micro Focus announced their intent to merge HPE’s non-core software assets with the Micro Focus suite of solutions, a deal valued at USD $8.8 billion.
Both announcements represent HPE’s plan to slim down and to focus on its primary strategy – to become the industry leader in supplying software-defined hybrid IT solutions that will run today’s data centers and will bridge them to multicloud environments. Core software assets such as OneView and the Helion Cloud platform remain with HPE. It is the non-core assets that are being spun off. The Availability Digest reviews HPE’s strategy and introduces readers to the new realm of “spin-merge.”
In addition to “HPE Spins Off Software Assets to Micro Focus,” read the following articles in the Availability Digest’s September 2016 issue:
ING Bank Down Ten Hours Due to Fire Suppression Test – Inergen fire suppression systems are popular and necessary add-ons in data centers. So important are they that tests of the systems are scheduled routinely. Here lies a big challenge. The release of Inergen gas is explosive and very, very loud. Coupled with the noise of the fire sirens, the threat exists that unless precautions are taken, hard disks can be damaged. Such was the case to WestHost in 2010. Now comes another example – ING Bank in Bucharest, Romania, lost its data center for 10 hours during a recent test of its fire-suppression system.
Yahoo Hack Sets a Record – 500 Million Accounts – Not every record-breaking accomplishment deserves to be lauded. In late 2014, a Yahoo data breach led to the theft of information from 500 million user accounts – the largest corporate breach ever reported. The breach was not discovered until much later and was not announced by Yahoo until September, 2016. What took so long?
Delta Air Lines Cancels 2,100 Flights Due to Power Outages – This past August, Delta’s data center in Atlanta, Georgia (USA) experienced a massive outage that cancelled over 2,100 flights and cost the airline at least USD $150 million in revenue. The culprit? A routine failover test caused a fire, which killed one of the two power feeds into the data center. That led to the discovery that hundreds of servers were not linked to an alternative power source. Redundancy matters.
@availabilitydig – The Twitter Feed of Outages - Our article highlights some of our numerous tweets that were favorited and retweeted in recent days.
The Availability Digest offers one-day and multi-day seminars on High Availability: Concepts and Practices. Seminars are given both onsite and online and are tailored to an organization’s specific needs. We also offer technical and marketing writing services for a variety of industries as well as consulting services on risk assessment and system architecture. We ghostwrite for others and have years of experience in writing patent disclosures.
Published monthly, the Digest is free and lives at www.availabilitydigest.com. Please visit our Continuous Availability Forum on LinkedIn. We’re at 781 members and counting. Follow us as well on Twitter @availabilitydig.
comForte - Events near you
|
EMEA |
|
|
|
Payment Knowledge Forum |
London, England |
Oct 3-4, 2016 |
|
GTUG National group |
Bad Homburg, Germany |
Oct 26-27, 2016 |
|
PCI Europe |
Amsterdam, Netherlands |
Dec 1, 2016 |
|
BITUG - Little SIG |
London, England |
Dec 8, 2016 |
|
USA |
|
|
|
DUST |
Scottsdale, AZ |
Oct 4, 2016 |
|
CTUG |
Mississauga, ON |
Oct 19, 2016 |
|
NENUG |
Andover, MA |
Oct 20, 2016 |
|
HP Technical Bootcamp |
San José, CA |
Nov 13-16, 2016 |
|
DUST |
Scottsdale, AZ |
Dec 13, 2016 |
Security Quiz
To ensure you and your security team are equipped with the right tools and knowledge necessary to keep Mars at bay, we have designed a security quiz to ready you and your team for battle. Be one of the first 100 people to take the test and get entered for a chance to win an Amazon Echo!
Steve
Tcherchian, CISSP
Chief Information Security Officer
XYPRO Technology
steve@xypro.com
comForte - With Yuma, NonStop X Has Become a Full Software Solution
30. Aug 2016 created by Richard Buckle | posted in: #Modernization #NonStopX #Yuma
It’s been almost a year since I first heard about Yuma in HPE Discover 2015 presentations and conversations. (Yuma is also known as NonStop Application Direct Interface, or NSADI). For anyone interested in NonStop systems, NSADI supports HPE’s message of how contemporary NonStop has become. Based on the Intel x86 architecture and utilizing industry standard InfiniBand (IB) as the interconnect fabric, NonStop has transcended both hardware and infrastructure to become a software solution – indeed, arguably, the best software platform on the planet.
It never comes as too big of a surprise when I hear adventurous developers mention NonStop on x86 and IB, sourced from vendors apart from HPE – particularly with the recent advances in virtualizing NonStop and its CLIMs. With vNonStop and vCLIMs, now all it takes is the presence of x86 chips, an appropriate Linux-supported KVM, and suddenly, vNonStop and vCLIMs will be impervious to what lies beneath. KVM? KVM provides the VM within which vNonStop and vCLIM can run. Transforming to a hybrid infrastructure suggests NonStop is part of the bigger picture for HPE in the data center.
Read the full story
Lusis TANGO Webinar Series
Please join us for our next series of 1-on-1 presentations on transaction processing software for acquiring, routing, switching and authentication.
TANGO is a solution that authorizes payments across multiple channels including ATM, POS, eCommerce, Prepaid and Mobile.
Learn how TANGO:
· Has become the most cost effective long term payments solution on the market
· Has been chosen by companies worldwide due to its performance and hardware agnostic capability
· Can offer flexible architecture while providing scalable performance
· Has recently gone live at one of the Big Five Banks in Canada
· Select a date and time that works best for you!
Register today: http://www.lusisblog.com/tango_webex.html
BRIAN MILLER
GENERAL MANAGER
Phone: 415-829-4577
Email: Brian.Miller@lusispayments.com
Website: www. lusispayments.com
XYPRO looks forward to seeing you throughout 2016
ATUG 2016September 29, 2016 September 29, 2016Atlanta, GAEvent Website >
Payments Knowledge ForumOctober 3, 2016 October 4, 2016LondonEvent Website >
DUST – October 2016October 4, 2016 October 4, 2016Event Website >
MATUG 2016October 18, 2016Event Website >
PCI Europe 2016October 19, 2016 October 20, 2016Edinburgh, ScotlandEvent Website >
CTUG 2016October 19, 2016 October 20, 2016Mississauga, Ontario, CanadaEvent Website >
NENUG 2016October 20, 2016Event Website >
GTUG SIGOctober 26, 2016 October 27, 2016Bad Homburg v. d. Höhe, GermanyEvent Website >
NonStop Technical Boot Camp 2016November 13, 2016 November 16, 2016San Jose, Ca.Event Website >
PCI Asia Pacific 2016November 16, 2016 November 17, 2016SingaporeEvent Website >
comForte - Webinar: Modernizing Payment Applications on the NonStop Platform: Hype or Hope?
The Payment landscape is evolving fast as payment processors and banks struggle with new competitors and regulations. Fintech start-ups challenge every assumption and technology by starting from the bottom – while new regulations such as GDPR (new European privacy laws) are difficult to implement in legacy systems which have grown over decades.
The key to effective, efficient operations for IT - and your company - is not to radically replace core business offerings or functionality of legacy applications but rather to use a smart modernization approach. Fortunately, with the right tools and expertise, it’s possible to cost effectively modernize payment applications running on the NonStop platform, which itself has recently been modernized by HPE.
‘Modernization’ can mean anything from connecting your existing application to new market players to extending the capabilities ‘in-place’ - to improving security and governance/compliance.
XYPRO is proud to be a Diamond Sponsor for this year’s NonStop Technical Boot Camp!
With over 500 NonStop community members expected to attend, this is an event that you don’t want to miss! At XYPRO excitement is building and we are enthusiastically planning educational presentations, product updatesand fun nights out on the town. Visit www.NonStopBootcamp.com for the latest information on pre-conference seminars, the session agenda and the exciting speakers lined up! If you have yet to register for both the Pre-Conference Seminars and the Boot Camp get signed up now. We cannot wait to see everyone; this should be the best Boot Camp conference yet!!
comForte - Technical Boot Camp website
Join us at the NonStop Technical Boot Camp in San Jose!
We are excited to be a Diamond Sponsor at the Technical Bootcamp and are looking forward to seeing you in one of our pre-conference seminars, presentations or at our stand in the Partner Pavillion.
Visit our website for more information on our presentation
Musings on NonStop!
September, ‘16
The
opinions expressed here are solely
those of the now self-employed author
Are you finding this format for my Musings on NonStop useful? Do you find the links to my posts and commentaries worth following? It’s been a year since I changed the content of my monthly Musings but I am always monitoring the results – so if there are any suggestions you would like to make, feel free to email me at: richard@pyalla-technologies.com And if you plan on attending a couple of RUG meetings including DUST and CTUG, come and say Hi!
Continuing with these thoughts,
who within the NonStop community these days doesn’t have a LinkedIn
profile? On the other hand, even as LinkedIn constantly fine-tunes their
product offerings, the amount of information crossing our desks / laps
continues to climb. Have we reached saturation point where reading
anything more has become information overload? Again, we are only a
couple of months away from the NonStop Technical Boot Camp (TBC) and
even as I look forward to catching up with many of you, I am open to
changing style and formats to better suit the time you can spend staying
current on all things NonStop.
Perhaps the overriding issue this month concerns just how many more
changes can we expect to see occurring at HPE? There’s scarcely a week
that passes where HPE isn’t making headlines – first with the now famous
“spin-merge” of HP Enterprise Services (Services) to / with CSC and more
recently, the additional spin-merge of HP Software (Software) with Micro
Focus. Along the way there was the small news item concerning the
purchase of SGI – a famed label within Silicon Valley but not a company
that shared anything today with its former glorious past. However, HPE
now has a top-end, scale up, option for the SuperDome X product line
even as it generates further options for those running SAP-HANA
in-memory.
However, it is the new focus by HPE on infrastructure and platforms that
has caught my attention as has the realization that today, NonStop is
the best software “platform” on the planet. And how fortunate was if for
NonStop to be considered within HPE as a platform! If you missed the
December 15, 2016, post
Picking the line … to the NonStop community blog, Real Time View,
then you may want to revisit the observations I made and the direct
quote from then HPE CTO, Martin Fink. Midway through the post you will
read of my encouragement to truly reconsider the future of NonStop
systems as HPE has clearly made a sizable investment in its future even
as it turns up the heat on the value proposition of NonStop systems –
there’s little confusion or ambiguity about the intentions of HPE
concerning NonStop. “NonStop X? It’s the best software platform on the
planet!”
NonStop isn’t going anywhere even as Mission Critical Systems (MCS) at
HPE, the home of NonStop, has become part of the Data Center
Infrastructure Group (DCIG). This group is one of three that has been
created in the new look HPE: it recently formed three core business
groups within HPE's Enterprise Group division - one focusing on
software-defined and cloud technologies, one focused on data center
infrastructure, and one focused on edge technologies and the internet of
things. But for more on this most recent development, look for next
month’s Musings where I will have even more to say on the matter. In the
meantime for all the coverage I have given to HPE and NonStop of late,
check out the links below to the posts and commentaries for the month of
August.
Real Time View:
And this month I wrote a fourth post as I celebrated the commencement of
my tenth year of blogging!
http://itug-connection.blogspot.com/2016/08/time-to-reach-for-big-guns-fighting-for.html
http://itug-connection.blogspot.com/2016/08/where-do-we-turn-for-news-for-nonstop.html
http://itug-connection.blogspot.com/2016/08/you-want-to-read-more-posts-on-nonstop_20.html
http://itug-connection.blogspot.com/2016/08/inside-numbers-when-being-1-matters.html
LinkedIn blog / Pulse:
Becoming my go to place for short
commentaries and where I have now published 50 posts!
https://www.linkedin.com/pulse/bizcations-how-we-all-working-future-richard-buckle?trk=mp-author-card
https://www.linkedin.com/pulse/supporting-my-clients-want-know-which-linkedin-groups-richard-buckle?trk=mp-author-card
https://www.linkedin.com/pulse/nonstop-vendors-continue-support-system-managers-usage-richard-buckle?trk=mp-author-card
https://www.linkedin.com/pulse/start-my-tenth-year-blogging-expect-see-many-more-posts-buckle?trk=mp-author-card
https://www.linkedin.com/pulse/boot-camp-coming-yes-once-again-omnipayments-hosting-reception?trk=mp-author-card
As well as a three part post on
storage …
https://www.linkedin.com/pulse/bridging-data-gulch-part-1-richard-buckle?trk=mp-author-card
https://www.linkedin.com/pulse/bridging-data-gulch-part-2-richard-buckle?trk=mp-author-card
https://www.linkedin.com/pulse/bridging-data-gulch-part-3-richard-buckle?trk=mp-author-card
ATMmarketplace:
http://www.atmmarketplace.com/blogs/in-the-mood-to-steal-you-might-be-out-of-luck/
Banking Technology:
http://www.bankingtech.com/555822/lets-all-get-together-not-likely-mobile-payments-are-still-a-far-far-away-dream/
ComForte:
https://comforte.com/blog/blog-article/hpes-the-machine-what-it-means-for-nonstop/
https://comforte.com/blog/blog-article/with-yuma-nonstop-x-has-become-a-full-software-solution/
Tandemworld (Musings on
NonStop):
Where you will find a collection of posts
and articles in support of IR, DataExpress, TCM Solutions as well as my
monthly Musings on NonStop:
http://www.tandemworld.net/newsletter_aug16.html
Buckle-Up-Travel:
http://buckle-up-travel.blogspot.com/2016/08/july-vacation-no-time-to-spare-so-how.html
Richard Buckle
Cofounder and CEO
Pyalla Technologies, LLC
Email:
richard@pyalla-technologies.com
TCM Solutions - providers
of HPE NonStop Remote Systems Management
for 20 years without fail
With our eyes never far away from what our customers are doing and as we maintain regular contact with our colleagues at HPE, there is much that we are learning of late. It seems that there has been a sizable jolt that has passed through the NonStop community that has awakened many of our customers to just how good they are having it; running critical applications on NonStop is, once again, making sense to them. Historically, the banks we work with have been NonStop stalwarts for decades but many of our colleagues that we had dealt with over the years were considering career changes as they looked to develop skills on platforms apart from NonStop. It was only a year or so ago that we noticed a lot more chatter taking place about just how long NonStop could prevail.
Despite renewed commitment to the NonStop platform, there is a number of
NonStop users who will more than likely encounter critical staff
shortages in the near term and for a couple of easily-observable
reasons. Just take a look at the numbers of the new NonStop X systems
HPE is telling us all have been ordered and, in many instances, already
shipped. The signs were there that the marketplace would welcome greater
standardization and openness, and getting considerable price performance
benefits has NonStop being considered for running even more
applications, and it’s not just in banking as we see signs too of
renewed interest in NonStop here in Europe among the manufacturing and
distribution industries.
It has been hard to miss the industry-wide shake out that is happening –
and for many in the NonStop community, it’s been hard to keep our eyes
off the headlines appearing almost daily. Dell goes private, buys EMC
and then sells its burgeoning software business to a group of investors
from the private equity marketplace. We have seen too a number of
financial analysts speculate about IBM having failed to sell its
mainframe business even as there is now renewed focus on some of IBM’s
key software products that are possibly up for sale. At HPE, the changes
too keep on coming.
The dust has barely settled on news of HPE buying SGI when fresh
headlines proclaim that HPE is shopping its entire software unit to
numerous private equity firms, and last week, the odds-on favorite to
pick up all of HPE software was a company few would be familiar with -
Thoma Bravo. But that was early in the month while now we know that HPE
has gone with MicroFocus. In the
HPE press release, Meg Whitman HPE CEO, said, “When we launched the
new HPE, we laid out a vision of being the industry's leading provider
of hybrid IT, built on the secure, next-generation, software-defined
infrastructure that will run customers' data centers today, bridge them
to multi-cloud environments tomorrow, and enable the emerging
intelligent edge that will power campus, branch and IoT applications for
decades to come.”
Furthermore, according to Whitman, “To achieve this vision, we've been
busy realigning our portfolio and product roadmap with our go-forward
strategy … through this process, we also identified areas of the
business that were not aligned with our go-forward strategy. And today
we announced plans for the spin-merge of our non-core software assets
with Micro Focus. The combination of HPE’s Application Delivery
Management, Big Data, Enterprise Security, Information Management &
Governance and IT Operations Management businesses with Micro Focus will
create one of the world’s largest pure-play software companies.” Of
course, Dell completing its acquisition of EMC will likely tell you
something similar as they too had already spun off their software
division as well to private equity firms including
Francisco Partners and Elliott Management.
If you take all this activity among major systems vendors at face value
it would appear that each of them is looking at how to best respond to
the inroads being made by clouds. The numbers being given for the
savings that can be generated by embracing clouds seem to be enticing
many enterprises to take cloud computing very seriously and it’s proving
just as hard to miss how enterprise vendors, including HPE, have
elevated hybrid infrastructures to being a major component of their
messaging. The whole point about transforming to a hybrid infrastructure
revolves around the sensible premise that you can keep your traditional
IT while you add private clouds – all while exploiting new APIs made
available for the sole purpose of simplifying the integration between
traditional IT and clouds.
However, even as we stay close to our customers the signs of real
progress in this area are somewhat low-key for the moment. There is a
reason why NonStop has served users well for such a long time –
unparalleled levels of availability, such that enterprises move very
slowly when it comes to changing any part of their mission critical
environment. This is real money that could be affected and no enterprise
is in a hurry to mess with the generation of additional income for the
enterprise. And yet, even among NonStop’s staunchest alleys, the signs
are all there that baby steps are being taken towards embracing hybrid
infrastructures. Solutions vendors are beginning to align their product
offerings to capitalise on the flexibility and indeed lower costs that
can come with deploying hybrid infrastructures.
It is also hard to miss the need for additional skills at these
enterprises. Knowing just NonStop, or just Linux, or indeed,
increasingly so, mixes of operating systems and hypervisors (given the
imminent arrival of virtual NonStop) that are becoming commonplace will
become a liability for many. Within the NonStop community, this will
prove to be a stumbling block when it comes to moving beyond Proof of
Concepts and Pilot deployments. That’s where managed services, such as
TCM come to the rescue! As we continue to watch the industry and we
watch the progress being made by our NonStop customers we are very aware
of their future requirements and we are taking steps to ensure we are
right with them as their needs develop; be it with our on-site services
or our 24 x 7 low cost cloud based and remote services – it’s just what
we have been doing for several decades now.
The value that comes from working with a proven provider of managed
services such as TCM, with over 2 decades of mission critical service
delivery experience is pretty obvious as it is easy to see what is
happening across the industry and inside the enterprise. In our last
article to Tandemworld we wrote about who is left to manage NonStop but
now, we can go one step further. Who are you contacting to manage your
NonStop systems for the future? We at TCM look forward to hearing from
you as yes, we continue to serve the NonStop community with reliable
cost-effective solutions, even as what constitutes a modern NonStop
system changes fundamentally and, from our perspective, fundamentally
for the better!
Kind Regards
Tony Craig
Managing Director
TCM House, NonStop Centre of Excellence,
Saltire Centre, Pentland Park, Glenrothes, Fife, KY6 2AG
www.tcm.uk.com
+44(0)1592 770081
Find out more about us at www.tandemworld.net
+44 (0) 20 8304 7979
We would like to thank the sponsors of the September 2016 eNewsletter
Platinum Sponsor is
Gold Sponsor
Silver Sponsor
To enquire about Sponsorship opportunities for the Tandemworld Newsletter please click here.
Current Subscribers 15102
Our company, Tandemworld, accepts no
liability for the content of this email, or for the consequences of any
actions taken on the basis of the information provided.
To Unsubscribe or Change your Subscription
Please click here


