
NonStop ™ eNewsletter for June 2018
June 2018 Sponsor
________________________________________
Contents
OmniPayments brings blockchain-based Fraud Prevention and KYC/AML
Mark Your Diaries eBITIUG 2019
Master your Java applications better than ever before
Gravic Publishes Article on the Better Backup Method
Raymond James integrates key enterprise applications with the NonStop
Registration Now Open for the MATUG Fall Users Meeting
Greetings from Big SIG & GTUG 2018!
GDPR and TW
XYPRO partners with CyberArk and SailPoint to maximize enterprise identity governance and security investments for HPE NonStop server
Everything in one place with Reflex 80:20
Moving towards the Hybrid Cloud
Visit the XYPRO events calendar to see where we will be and sign up for free webinars
CIBC COMPLETES MIGRATION TO LUSIS TANGO PAYMENTS SYSTEM
HPE NonStop Security Provider XYPRO Granted Patent for Contextualizing Multiple Security Events
Availability Digest Investigates Redundancy Vs. Backups
Registration is open for the 2018 NonStop Technical Boot Camp!
ASK
OmniPayments brings blockchain-based Fraud Prevention and KYC/AML

In the fight against payment fraud, banks and card processors are finding that many of the traditional rules no longer apply.
In the past, banks could set up their software to detect for a set of known rules. So for example, children’s or minor’s cards being presented to buy goods in the late evening would trigger an alert, as would the same cards being used to buy alcohol or other goods prohibited to those of similar age profile. Another would be the source of the transaction - geo-location enables the bank or Card Processor to know if the transaction was initiated, for example, in any suspect part of the world.
Today however, sophisticated fraudsters know many of these rules and how to work around them. Cybercriminals can be several steps ahead of their bank victims, so the banks must closely observe the behaviour of people to spot when something looks wrong.
In the modern world, we don’t know always know where the dangers are coming from, so OmniPayments are in collaboration with its clients to create innovative KYC solutions using R3 Corda (aka Blockchain) so that institutions can quickly respond to and report Anti-Money Laundering (AML) situations. As the Corda system gathers an increasing amount of data, reliable KYC and AML functions become a lot easier to automate removing cost and risk from Banks and Card Processors. As the Digital banking world demands banks increase automation to maintain their risk, costs, and profitability, we are likely to see more instances where solutions like the OmniPayments KYC/AML solution play their part.
OmniPayments KYC/AML solution is OmniPayments latest member of the Fraud Management suite, bringing greater value to clients who need to prevent their fraud before it costs them dear. The OmniPayments Fraud Management suite includes the real-time Fraud Blocker, a core component for preventing Fraud before it happens, reducing the burden on the compliance and risk departments, and more importantly reducing Financial loss.
Reach out to us to learn more.
Mark Your Diaries eBITIUG 2019

Master your Java applications better than ever before
Common tools for APM of Java can only manage a fraction of complex applications written in Java. This is not good enough!
ITP-PANORAMA can master unlimited amount of Java code. Largest number LOC scanned so far is 240 Million.
It was never before possible to overview and analyze all Packages, Classes and Methods of an enterprise at the same time. ITP offers now both Eclipse or IDz user interface.
Performing analyses, searches and selections used to be time consuming.
The repository of ITP-PANORAMA resides in the RAM of a server in a propriety multidimensional OLAP HyperCube repository. No need to access data outside the RAM during analyses, searches or selections.
Response time is less than a 3 second in average, because all happens in the memory. In addition, all available processors are used simultaneously.
So far, Change Requests and so the “time to market” take too long and are too expensive. There is always a risk that architects and developers overlook the impact of a change to the entire software system.
Results of analyses, searches and selections performed with ITP-PANORAMA are always 100% correct and reliable. This is because a Cross-Reference-Check is performed during scanning and all entities that are retrieved from the source code are linked with all usages.
Developers save 90% of time analyzing the impact of a change request to the entire software system when compared to common tools
Installation takes only two or three days. Training 4 – 6 hours.
For more information and a fact sheet: juergen.overhoff@itp-panorama.com
Gravic Publishes Article on the Better Backup Method

Gravic recently published the article, The Better Backup Method, in the May/June issue of The Connection. This article discusses strategies for improving database recovery times after catastrophic failure for companies that use the “tried-and-true” backup and restore approach for data recovery. This method focuses on reducing the amount of data that needs to be backed up, stored, and subsequently retrieved for restoring transactional mission-critical databases to a current, consistent, and complete state in order to continue processing. It also focuses on the so-called online backup problem (where the database is open for processing while the backup occurs), and uses several techniques to reduce the amount of data that must be stored while the backup is taking place as well as for the subsequent changes to the data after the backup completes. Since there is a growing need for an economic and efficient way to back up very large-scale databases, many companies are returning to physical tape to fill this need. The better backup method significantly and efficiently uses backup media and backup/restore processing to improve current techniques.
Gravic Presents at NENUG, NYTUG, N2TUG and LATUG Regional Meetings
Attendees enjoyed our presentation, HPE Shadowbase Use Case Solutions & Product Update, at several recent meetings including, NENUG (Andover, MA), NYTUG (Berkeley Heights, NJ), N2TUG
(Dallas, TX), and LATUG (Santiago, Chile). We described how HPE Shadowbase works in several use cases for these solution categories:(active/passive through active/active replication systems)
We also reviewed new and future HPE Shadowbase product features, including support for DB2 as a source, Enscribe to SQL replication enhancements, further improvements that simplify migrating from RDF or OGG to HPE Shadowbase, and additional BASE24™ feature support. Prior to LATUG, we also co-sponsored an informative and productive Partner Technical Update (PTU) for HPE Sales, Technical Services, and Solution Architects.
To speak with us about your data replication and data integration needs, please call us at +1.610.647.6250, or email us at SBProductManagement@gravic.com.
Hewlett Packard Enterprise directly sells and supports Shadowbase solutions under the name HPE Shadowbase. For more information, please contact your local HPE Shadowbase representative or visit our website.
Please Visit Gravic at these Upcoming 2018 Events
|
ATUG Meeting—Atlanta, 19 September |
|
CTUG Conference—Toronto, 26-27 September |
|
MATUG Meeting—Baltimore, 28 September |
|
MEXTUG Meeting—Mexico City, 4 October |
|
Connect HPE Technical Boot Camp—San Francisco, 11-14 November |
Raymond James integrates key enterprise applications with the NonStop - from POC to production in less than 4 months with NuWave !
Within the NonStop user base, modernization is rightly viewed as an effective method to meet changing business requirements more quickly. However, when it comes to actually modernizing NonStop applications there are a number of different approaches to choose from.
A NuWave case study details how Raymond James recently modernized their core NonStop applications to allow them to quickly address new business requirements.
Jes Thamdrup of Raymond James explains how they've used SOAPam® Client to quickly and easily integrate their NonStop applications with other parts of the enterprise: Integrating NonStop Applications with Third-Party Web Services
Registration Now Open for the MATUG Fall Users Meeting

Please register via EventBrite
for the Mid-Atlantic Tandem User Group (MATUG) meeting scheduled for 8am-5pm on Friday, September 28, 2018 at the DoubleTree by Hilton Hotel Baltimore-BWI Airport near Baltimore, MD, USA. (Click https://eventbrite.com/event/16902004350/ for more information.) Expect HPE presentations on the NonStop HW/SW product roadmap and new technology with blockchain, as well as several informative vendor presentations.Calling all VENDORS, ISV’s, and SOFTWARE PROVIDERS: There are only four 25-minute vendor presentation slots still available, for a reasonable sponsorship fee (TBD based on overall meeting expenses, including meals and estimated to be around $500). These slots will be filled on a “first-come first-serve” basis, based on the time of your email response to Susan Loeliger, MATUG Secretary/Treasurer. (User presentations take preference and are free.)
The MATUG meeting is open to all HPE NonStop customers, partners, users, consultants, or interested parties. Members are usually from the following states: Pennsylvania, New Jersey, Maryland, Delaware, Virginia, Washington, D.C., and West Virginia, although anyone can attend. MATUG provides members with the opportunity to participate in quality informational sessions, learn about new HPE products and services, and interact with fellow HPE NonStop users. Please forward this announcement to others in your organization who may be interested in attending.
Greetings from Big SIG & GTUG 2018!
Hello and Guten Tag! The CSP team was on hand for the 2018 Big SIG, London and GTUG, Leipzig conferences.
BITUG Big SIG 2018 returned to London's Trinity House on May 9th and CSP's Chief Technical Officer, Callum Barclay, discussed Multi-Factor Authentication on NonStop systems during his plenary presentation. This is a critical security requirement, which relates to PCI-DSS and the newly introduced GDPR legislation. Our latest solution, CSP Authenticator+ is perfectly suited for managing these new requirements.

Connect Deutschland and the German NonStop User Group (GTUG) hosted the eight annual European NonStop HotSpot Conference and Exhibition, which took place at the Westin Hotel Leipzig, situated in the heart of one of Germany’s most lively and historic cities. CSP was proud to be a platinum sponsor of this outstanding event.

The CSP team introduced the latest updates to Protect-X®, version 4.0, which include Guardian file permissions management, Guardian user/alias management & compliance, OSS file security management & compliance, and support for multi-factor authentication. We had a packed auditorium and really appreciate the feedback received during our Q&A. We would like to thank all those who attended our presentations.
It was a pleasure speaking with all of the attendees who stopped by the CSP booth to chat about our latest solutions.
We would also like to thank both the BITUG Big SIG and GTUG/ Connect organizers for putting together these exceptional events.
We look forward to seeing you again at the next event. Until then, Auf Wiedersehen!
For more information on CSP solutions visit
www.cspsecurity.comFor complimentary access to CSP-Wiki®, an extensive repository of NonStop security knowledge and best practices, please visit
wiki.cspsecurity.com
We Built the Wiki for NonStop Security ®
Regards,
The CSP Team
+1(905) 568 - 8900

GDPR & TW
GDPR: On 25th May 2018, a new European Union (EU) data protection law, the General Data Protection Regulation (GDPR), takes effect. The GDPR gives individuals in the EU more control over how their data is used and places certain obligations on businesses that process information of those individuals. We are updating our Policy to take into account the new requirements of the GDPR.
In accordance with this we need your permission to continue to send you emails relating to the Nonstop World (Tandemworld) Limited eNewsletter and the products and services that you can purchase from Nonstop World (Tandemworld) Limited
Preferences
It is extremely important that you update your preferences with us, to comply with the new GDPR regulations – simply click one of the following links, to confirm your mailing preferences.
The only data we collect and hold is your email address. We collect no further information.
XYPRO partners with CyberArk and SailPoint to maximize enterprise identity governance and security investments for HPE NonStop servers
XYPRO partners with CyberArk and SailPoint to maximize enterprise identity governance and security investments for HPE NonStop servers.
Integrate HPE NonStop servers with CyberArk Enterprise Password Vault
Expanding on the recent strategic SailPoint partnership and integration for the HPE NonStop Server, XYPRO is thrilled to announce our partnership with CyberArk, a leader in digital vault and privileged access management technology.
One of the most severe security risks to any organization is stale privileged accounts or the misuse, compromise or sharing of those accounts. Privileged accounts have elevated access to perform administrative type functions. They can be administrator accounts, service accounts, firecall or emergency accounts, database connection accounts, applications accounts among others.
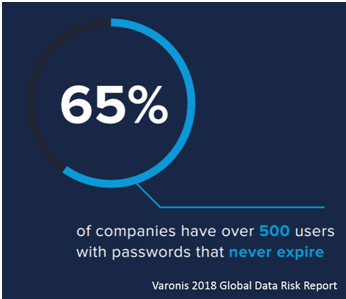
Most of these accounts were set up ages ago when an application or system was deployed. They typically have multiple integration points and because of the risk of “breaking something”, the passwords for these accounts are rarely rotated, likely shared and improperly stored. According to the Varonis 2018 Global Data Risk Report – 65 percent of companies have over 500 accounts with passwords that are never rotated. Passwords that are never rotated or rotated on an infrequent basis, have a higher likelihood of showing up in online password dumps and used to infiltrate networks. Privileged and service accounts with non-expiring passwords are a cyber criminal’s best friend. Ensuring privileged account passwords are stored properly, changed regularly, meet complexity and compliance requirements, and are audited can be overwhelming to implement and manage. Current solutions for requesting and managing access to privileged accounts are manual, complex, and frequently do not map to the core business initiatives. Governance is often an afterthought, leaving many enterprises vulnerable to increased security risks and potential non-compliance with external regulations or internal corporate mandates.
To address this need, XYPRO has been working closely with CyberArk and our customer base to deliver the only supported CyberArk integration for the HPE NonStop server. XYPRO’s newest offering, XYGATE Identity Connector for CyberArk, bridges the gap between identity governance and enterprise password management for the HPE NonStop server.
CyberArk’s Enterprise Password Vault (EPV)
enables organizations to secure, manage, automate and log all activities associated with privileged accounts. In today’s ecosystem where privileged account abuse is the most common way for hackers to compromise a system, proper credential storage and accountability is paramount in risk mitigation. Relying on manual methods is resource intensive, error prone and leaves gaps. A password vault is the ideal solution for automating these activities and addressing compliance needs. Using CyberArk’s EPV, you will gain additional benefits such as:
- Leveraging existing IT infrastructure
- Policy enforcement at an enterprise level
- Automatic password rotation
- Full auditing of who accessed credentials
- Integration with SIEMs
CyberArk EPV allows you to take advantage of robust workflows that help enforce and streamline password policies and maintenance.
Using XYGATE Identity Connector (XIC), your HPE NonStop servers can now seamlessly integrate with your CyberArk® Enterprise Password Vault (EPV), allowing end-to-end password management of NonStop privileged accounts, such as SUPER.SUPER.
Why Integrate your HPE NonStop servers with CyberArk EPV?

An organization typically stores privileged accounts and passwords, including NonStop credentials, within the CyberArk EPV. A user then requests and is given access to a privileged NonStop account for a specified amount of time – for example, they are granted SUPER.SUPER access for four hours to complete a certain task. Once approved, CyberArk releases the password to the user. When that four-hour time window expires, CyberArk expires the current password within the vault and assigns a new one. Without XYGATE Identity Connector for CyberArk, the new password in CyberArk and the one on the NonStop server fall out of sync. It is then incumbent upon the CyberArk administrator to communicate to the NonStop administrator and ask them to update the password via a manual process to keep it in sync with CyberArk EPV. This manual process is typically via insecure methods such as email, SMS or simply writing it down in a text file stored on someone’s desktop. What is even riskier is that until this manual process is completed, which can be hours or days, the NonStop user originally granted access for only four hours has access to the privileged account the entire time, much longer than was authorized. This time-consuming process is also a huge security risk and compliance issue. Using XYGATE Identity Connector for CyberArk, this process becomes automated, updating the NonStop server as soon as the password is rotated in the CyberArk EPV, ensuring the user who was approved for access to the privileged account for four hours cannot log on to that account after the authorized time window has expired.
Most organizations already have active projects to extend their existing CyberArk and SailPoint investments into the rest of the enterprise platforms, processes and applications, of which the HPE NonStop will now be one of those integrations.
XYGATE Identity Connector for CyberArk comes packaged as a lightweight, easy to deploy, executable using a micro service framework that runs on your existing NonStop servers. Simply configure the service XML with the specific HPE NonStop server properties and run the deployer. XYGATE Identity Connector deploys quickly in a JAVA Virtual Machine (JVM) on OSS. No other software is required. Installation is simple, quick and secure. XYGATE Identity Connector for CyberArk supports both HPE NonStop user accounts and aliases.
Configuration from the CyberArk side is just as easy. Ensure you are using CyberArk Enterprise Password Vault version 9.x or above. Then simply log into the CyberArk marketplace and download the XYPRO CPM Plugin for HPE NonStop. Once installed, this enables connectivity between your vault and the XIC instance running on the HPE NonStop server via REST Web API. Configure your IP address, port and credentials to connect to XIC and immediately begin vaulting your passwords and taking advantage of all your already established corporate policies within CyberArk.
Why integrate your HPE NonStop with SailPoint
IdentityIQ?
Complementing our new CyberArk partnership and integration is our HPE
NonStop integration with SailPoint that we announced in March 2018.
Without centralized identity management, onboarding and off-boarding activities become a manual process, which is not only time consuming but introduces unnecessary security risk and compliance concerns. XYGATE Identity Connector for SailPoint provides complete control over who has access to your NonStop servers from a single enterprise location.
XYPRO’s XIC solution simplifies requirements and compliance activities. When an identity is disabled through SailPoint IdentityIQ, the corresponding account is immediately disabled on all NonStop servers on which the identity was provisioned. When that identity is removed using IdentityIQ, the account is immediately removed from all NonStop servers, ensuring the removal of stale accounts, improving your relationship with your auditors and strengthening your security procedures at the same time.
Using XYGATE Identity Connector for SailPoint, HPE NonStop customers can now integrate their NonStop servers with their SailPoint IdentityIQ, enabling seamless participation within the enterprise.

SailPoint’s industry-leading, powerful access certifications, governance controls and logical workflows allow NonStop customers to take full advantage of the capabilities provided by SailPoint that have long been available for other platforms.
To learn more about XYGATE Identity Connector, please contact your XYPRO Account Executive or visit www.xypro.com/identity.
Steve Tcherchian, CISSP
CISO and Director of Product
XYPRO Technology
Steve Tcherchian, CISSP, PCI-ISA, PCIP is the Chief Information Security Officer and the Director of Product for XYPRO Technology. Steve is on the ISSA CISO Advisory Board, the NonStop Under 40 Executive Board and part of the ANSI X9 Security Standards Committee. A dynamic tech visionary with over 15 years in the cybersecurity field, Steve is responsible for strategy and innovation of XYPRO’s security product line as well as overseeing XYPRO’s risk, compliance and security to ensure the best experience for customers in the Mission-Critical computing marketplace
Everything in one place with Reflex 80:20
Software and technology companies operate in one of the most rapidly evolving industries of all, with immense shifts in development, infrastructure, customer expectations and business models. The ability to continually keep pace with these changes whilst grappling with fragmented business systems, siloed data and manual processes is increasingly hard.
The ability to consolidate information and make sense of relevant data streams is something that keeps many a CIO up at night. And this isn’t just limited to managing “big data”. We’re seeing an increasing trend of tools that offer a new look at workflow collaboration. Digital business demands a high degree of collaboration agility to improve team coordination. Slack, HipChat, Trello: these are relatively new tools that employ a SaaS model and aim to improve visibility of where workstreams are at any given time.
For any of these services to work effectively, a clear and concise dashboard is critical.
The advent of open source back end platforms such as Prometheus and Elasticsearch has enabled developers to focus on innovation rather than the burden of maintaining expensive hardware and software. Core metrics are displayed in traditional graphical format, but these are largely relied on by the developers themselves. The end users, for whom the product has been built, need a go to tool for communicating insights about a piece of data. Databoard and Tableau have recognised the desire for visualisation and offer an easy and scalable approach.
The importance of presenting critical information in graphical format has been a core component of our product development when it comes to NonStop monitoring.
The Reflex 80:20 Graphical Console is known as the OverDrive Status Monitor. The view represents the overall status of single or multiple NonStop nodes. OverDrive helps an installation to manage their NonStop nodes and active services by providing a graphical view of nominated exception conditions. Installations that need to manage their network other than “by exception” can witness a richer EMS event stream by using the OverDrive top-level views in conjunction with the text based Console facility. The OverDrive display is made up of columns known as Classes, and within classes, icons that can represent an underlying group of objects, or a single object. Classes can be built to represent subsystems, services or local user applications.
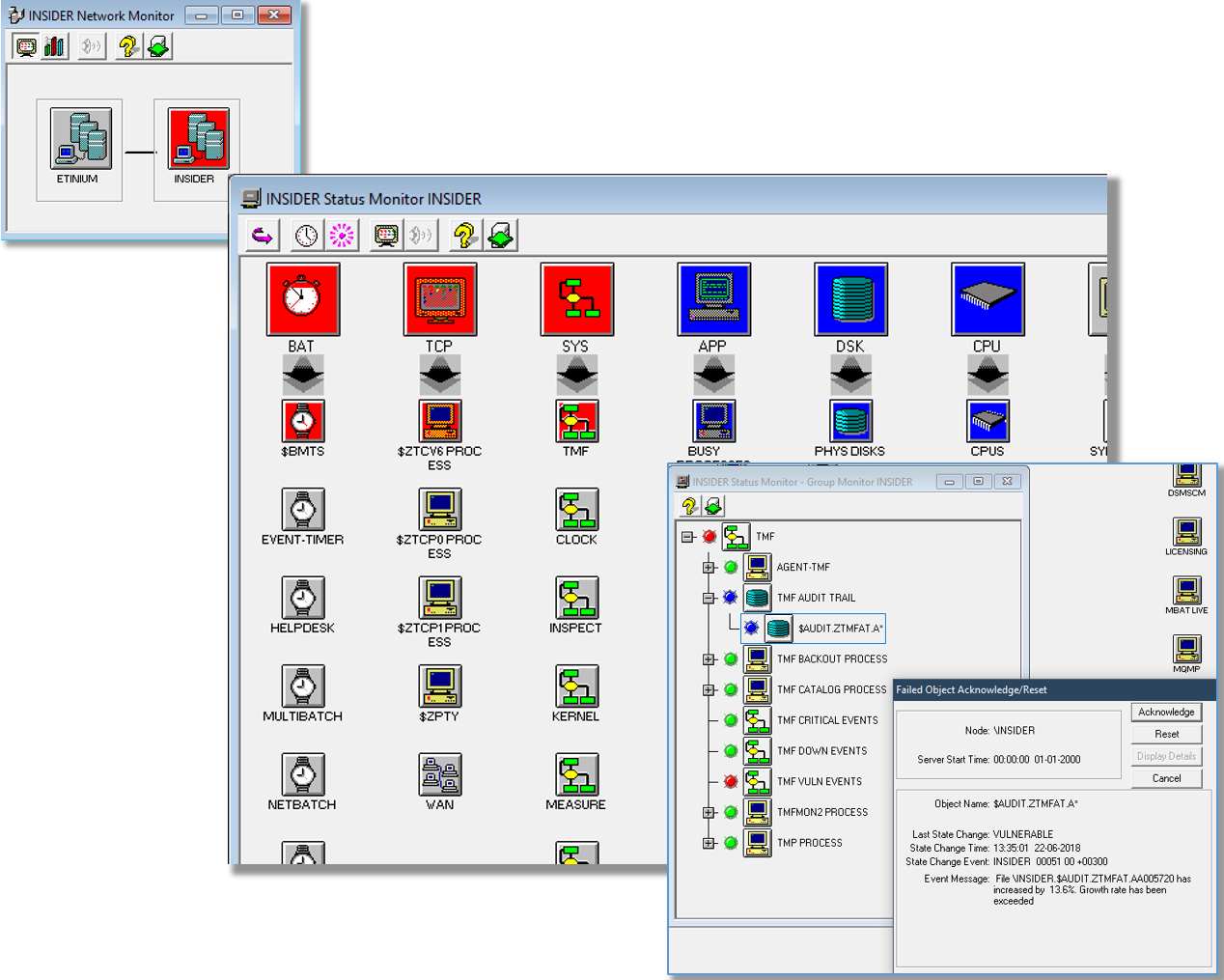
The structure of this display is completely at the discretion of the user. The most common approach is to create either status or service views. Status views are Operations driven where groups of “like” things, such as disk, spoolers, Pathways, are assembled into the same class. A service class however, could contain a set of process icons, a set of file icons, a spooler device and a specific communications line, all of which support an application. Either approach is acceptable and it is possible to implement both and have the same icon in more than one class. Icons can represent physical objects such as a communications line or a state such as “TMF Hung Transaction”. Icons in the OverDrive display can flash either blue (vulnerable) or red (down). Vulnerable is meant to illustrate that a service is continuing but that it is threatened.
This simple, yet highly effective visual interface ensures that NonStop operators can see exactly what is happening with the environment, and act accordingly.
Reflex is a highly cost effective solution that is trusted by some of the world’s most demanding organisations. We’d welcome the opportunity to discuss its capabilities, and how it should be a consideration for anyone moving to NonStop X.
|
|
Karl Gilbank |
Moving towards the Hybrid Cloud
By: Glenn Garrahan, Director HPE Business, Tributary Systems
and Shawn Sabanayagam, CEO, Tributary Systems
HPE Discover:
As HPE Discover wraps up in Las Vegas, Tributary Systems is excited about a 20 year long OEM contract supplying HPE with data backup/Restore and archive solutions. Tributary Systems looks forward to another 20 plus years of providing leading edge solutions to HPE and its customers - solutions like Storage Director high performance private and hybrid cloud data protection with Cloud Object Storage.
Take a moment to read this article:
https://tributary.com/wp-content/uploads/2018/01/TheCaseForCloudObjStorage.pdf
It’s the segue to another interesting article by Claudio Rubello Aranguren, Regional Technical Consultant, Technical Solutions, Hitachi Vantara. Claudio makes the point that by the year 2020 90% of all organizations will be in the hybrid cloud. Here are the top 5 reasons he cites for why this needs be a priority:
1)
Business Transformation2)
Lower Capex and Opex3) Business Volume Variability
4) Improved time to Market
5) System Speed and Scalability
Claudio provides a step by step guide for obtaining Hybrid Cloud buy-in within your organization:
How will NonStop customers take advantage of the hybrid cloud?
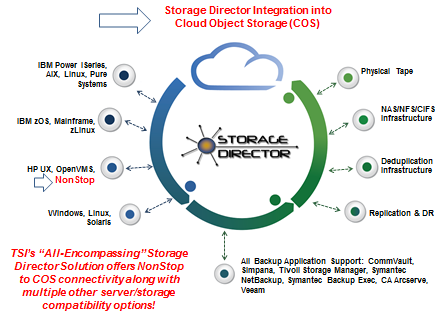
By employing Tributary System’s Cloud Object Storage Solution, that’s how. Employing advanced COS technology coupled with Tributary’s proven Storage Director® as the “front end”, NonStop customers can transparently take advantage of IBM’s Cloud Object Storage® (COS), formerly known as Cleversafe®, without any changes to their NonStop applications. In addition, Tributary’s software-defined Storage Director high performance front end ingestion and caching solution is now fully certified and approved for use with Hitachi Content Platform (HCP).
Storage Director, is a policy-based, tiered, and virtualized software solution especially designed for backup which can be seamlessly integrated with any media, including tapes, disk drives, virtual environments and NonStop or other proprietary server types, plus open systems. Storage Director can group data into different pools and apply different protection policies at different times across any storage medium simultaneously. Tributary Systems has gained a massive strategic edge as it has entered into synergistic partnerships with both IBM and Hitachi to revolutionize enterprise cloud data backup/restore, archive and DR. Combining the capabilities of Storage Director while endorsing long-term archival to Object Storage is where Tributary believes the data backup and retention market evolving, and sees no evidence to the contrary.
Tributary is the only company in the marketplace that can backup all NonStop mission-critical servers using a single solution. In addition to Storage Director’s AES 256-bit encryption, data is also erasure-coded in the storage tier.
From a performance standpoint, Tributary’s solution can ingest data at a rate of 12TB per hour and restore at about 8.5TB per hour. Should a flash storage be used in the cache layer, the ingestion rate goes up to 37TB per hour and restores at 35TB per hour; these performance metrics are unmatched in the market.
Tributary’s IP, when combined with leading Cloud Object Storage solutions imparts exclusive cutting-edge data storage and management capabilities that can be extended well beyond public cloud models—into hybrid and on- premise environments—and also offers double-layered security for NonStop clients.
Importantly, the Storage Director Cloud Object Storage solution can be implemented with a monthly fixed cost model unlike all public cloud providers such as AWS who charge customers for accessing their data through additional fees for “puts and gets.” Employing a cloud backup solution where costs vary widely from month to month, based on access to their own data, is challenging for most enterprise customers.
For more information visit
https://tributary.com/
Visit the XYPRO events calendar to see where we will be and sign up for free webinars

FREE WEBINAR: CyberArk and SailPoint: Maximize your investments in Identity Governance and Privileged Access Security*June 26, 2018WebinarEvent Website >

HPE KOREA Nonstop Technology Day 2018July 24, 2018Yeongdeungpo-gu, Seoul, South Korea - Conrad Hotel SeoulEvent Website >

HPE Taiwan Nonstop Technology Day 2018July 27, 2018Taipei City, Taiwan - Marriott TaipeiEvent Website >

ATUG 2018September 19, 2018Event Website >

CTUG 2018September 26, 2018 September 27, 2018Hewlett–Packard Enterprise Canada, 5150 Spectrum Way, Mississauga, OntarioEvent Website >

MATUG 2018September 28, 2018Linthicum, Maryland - DoubleTree by Hilton Hotel Baltimore-BWI AirportEvent Website >
CIBC COMPLETES MIGRATION TO LUSIS TANGO PAYMENTS SYSTEM
Lusis payment hub SOA architecture provides agility and scalability for an evolving marketplace
SAN FRANCISCO & PARIS--Lusis Payments, a global innovator of
mission-critical payments software, announced today that CIBC, a leading
Canadian-based global financial institution, has migrated its POS, ATM,
and Payments Hub to the Lusis TANGO platform. CIBC has been modernizing
its payments infrastructure to improve their ability to meet the demands
of today’s evolving payments ecosystem.
TANGO
is an online transaction processing engine for mission-critical 24x7
solutions including payments, retail, loyalty, finance, utilities, and
transport. TANGO delivers performance, availability, and scalability,
with a rich set of functionalities, all from a single application, a
single code set and a single architecture. This flexibility makes TANGO
ideal for the next generation of payment systems.
CIBC selected Lusis Payments’ TANGO product for use across a range of banking channels. TANGO allowed the bank to move to an open platform built on a high-performing micro-service architecture providing agile banking needs. CIBC has also implemented a number of new functionalities and capabilities to its payments systems as a result of the migration.
“TANGO is a payments HUB facing todays challenge,” said Philippe Preval, President and CEO of Lusis Payments. “TANGO is addressing business needs both now and in the foreseeable future. Our team worked closely with CIBC to provide the flexibility it needs in today’s evolving payments landscape.”
About Lusis Payments
Lusis Payments is an innovative global software and services provider to the payments industry. The company’s proven, cutting edge technology operates in numerous hardware and operating environments. The TANGO platform, combined with the know-how to mitigate risk and deliver high levels of assured customer service, constitutes a unique proposition for organizations faced with the challenge of adapting to traditional and future needs in the payments ecosystem.
Read the full article and Lusis New.
For more information about TANGO contact Brian Miller at
brian.miller@lusispayments.com or visit http://www.lusispayments.comBrian
Miller
Lusis Payments, North America
(415) 829-4577
Brian.Miller@lusispayments.com
HPE NonStop Security Provider XYPRO Granted Patent for Contextualizing Multiple Security Events
New security analytics technology to provide faster breach detection using patented security intelligence
“We are pleased that the US Patent Office recognized the innovative achievement of XYPRO,” said CEO Lisa Partridge. “Our method aggregates and correlates multiple data sources, including those not traditionally used for security monitoring. Our clients in banking, finance, telecom, retail, manufacturing and other critical sectors will find this new technology paramount in risk mitigation.” XYPRO’s patented method uses sources such as file metadata, system data and application data and applies a layer of platform and application specific context to determine if the newly created data is an actionable threat or not. The applied context can come from either a security context event map or from a machine learning algorithm generated by profiling the system over time to determine what context is normal for the given platform or application.
Availability Digest Investigates Redundancy Vs. Backups
Let’s be clear. The concepts of redundancy and backup are not the same.
Backup is about creating copies of data to protect against a
catastrophic loss. Redundancy refers to the ability to provide a
continuity of service, no matter what happens. Although both are
valuable tools for data archiving, redundancy and backup are not
interchangeable. How organizations choose to use them is as distinct as
the organizations themselves.
“Redundancy vs Backups” discusses the two concepts and explains the
differences. In addition to this story, read the articles below in the
Availability Digest.
Fault Tolerance vs Failure Tolerance – We’ve all heard of fault
tolerance. It is hardware or software that is built with redundant
components to ensure that processing survives the failure of an
individual component. But how many of you have you heard about failure
tolerance? It, too, is a term, albeit one not as popular. Failure
tolerance is defined as an application that can continue even when
failures such as a node or a site outage occur. Fault tolerance does not
require a backup system. Failure tolerance does. Failure tolerance also
requires an additional parameter – failover time.
TSB System Migration Costs 1300 Customers Their Savings – Talk about a
tough transition. TSB Bank is a retail and commercial bank in the UK.
Originally created by Lloyd’s Banking Group, TSB was sold in 2015 to the
Spanish bank Sabadell. So far, so good. All the problems arose when TSB
migrated from Lloyd’s legacy banking system to Sabadell’s system. In
April, 2018, the long-planned IT upgrade began, with TSB transferring
the records and accounts of its 5.2 million customers to the Sabadell
system. Sabadell announced that the migration was successful; yet three
weeks later, millions of TSB’s online and mobile remained locked out of
their accounts.
Fire Suppression Alarm Brings Down Nordic Nasdaq – It’s not the first
time the Digest has warned readers about the dangers of fire suppression
systems in data centers. In 2010, WestHost, a U.S.-based web-hosting
provider, suffered severe damage to most of its servers and data stores
dues to an accidental release of fire-suppressant gas. In 2016, a
fire-suppression test disabled an ING Bank data center in Bucharest,
Romania, for ten hours. In April of this year, the Nordic NASDAQ stock
exchange was forced to close for most of a day when the fire suppression
system in one of its data centers was triggered accidentally. It’s not
the gas that does all the damage. It’s the deafening noise that destroys
disk drives and damages servers.
@availabilitydig – The Twitter Feed of Outages - Our article highlights
some of our numerous tweets that were favorited and retweeted in recent
days.
The Availability Digest offers one-day and multi-day seminars on High
Availability: Concepts and Practices. Seminars are given both onsite and
online and are tailored to an organization’s specific needs. Popular
seminars are devoted to achieving fast failover, the impact of
redundancy on availability, basic availability concepts, and eliminating
planned downtime.
In addition, the Digest provides a variety of technical writing,
consulting, marketing, and seminar services. Individuals too busy to
write articles themselves often hire us to ghostwrite. We also create
white papers, case studies, technical manuals and specifications, RFPs,
presentation slides, web content, press releases, advertisements, and so
on.
Published monthly, the Digest is free and lives at
www.availabilitydigest.com. Please visit our Continuous Availability
Forum on LinkedIn. Follow us as well on Twitter @availabilitydig.
Registration is open for the 2018 NonStop Technical Boot Camp!

Make plans to join the global NonStop community for four days of networking and learning with NonStop Engineers, Executives, Partners and Customers at the Hyatt Regency San Francisco Airport:
Registration Information:
EARLY BIRD: $1395 (before 10/01/18)
REGULAR FEE: $1695 (after 10/01/18)
Call for Papers is OPEN:
Deadline for proposal is September 1st.
The Partner SIG looks forward to reuniting with Customers and HPE this fall in the Grand Peninsula Ballroom on the Lobby level!
Kathy Wood
NonStop Partner SIG/Vendor Chair
Ask TandemWorld
Got a question about NonStop ? ASK Tandemworld
Keep up with us on Twitter @tandemworld
We are currently seeking skilled resources across the EMEA region,
Find out more about us at
www.tandemworld.netJune 2018 Sponsor
+44 (0) 20 8304 7979
Our company, Tandemworld, accepts no
liability for the content of this email, or for the consequences of any
actions taken on the basis of the information provided.
To Unsubscribe or Change your Subscription Please click here

