Automated Conversion of HP NonStopTM COBOL applications to

NonStop ™ Newsletter for Aug 2021
______________________________________________
Current Global Subscribers 15,647 Click to Sponsor a Newsletter
Contents
Newsletters
Please Attend These HPE Shadowbase Presentations
at the NonStop TBC
NonStop
Technical Boot Camp 2021
PCI DSS 4.0 is Coming Will you be Ready?
A new TANGO Benchmark on HPE NonStop
ASK
XYPRO and HPE Partner to Provide ZERO Trust Security for HPE NonStop
The accelerating Growth of “Buy Now Pay Later”
NuWaves API Security Guide - Best Practices for REST Services
TANDsoft’s FS Backup and Restore – Say Goodbye to Whole File Backup
XYPRO to Present at HPE NonStop Technical Bootcamp 2021
Migration Services
Automated Conversion of HP NonStopTM COBOL applications to Java or C#
Migration of HP NonStopTM
COBOL applications is a serious and difficult undertaking. Decades of essential and proprietary processes that must be preserved are captured with the legacy code. Failure to replicate these critical business rules can have disastrous consequences. One should choose the migration vendor carefully based on skills, experience and migration technology used to minimize the risk and maximize the benefit.
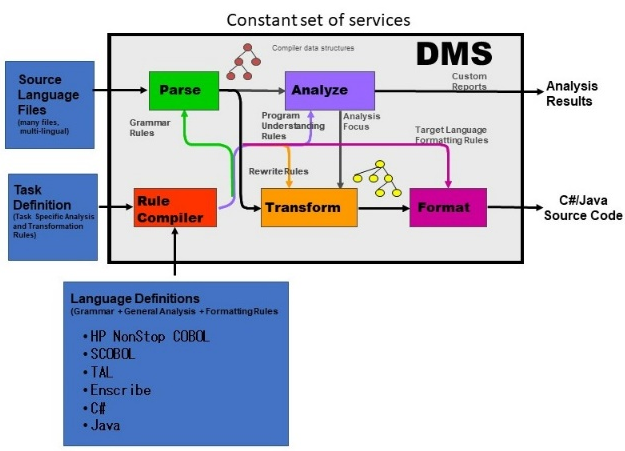
Semantic Designs offers highly accurate automated conversion of legacy HP NonStop COBOL/SCOBOL applications running on Tandem Mainframes to C#/.NET or Java platform running in a mainframe, server or cloud environment. Our HP NonStop COBOL /SCOBOL translators are built on top of Semantic Designs' advanced configurable compiler technology: DMS®.
With DMS, we are able to translate HP NonStopTM
COBOL applications to Java or C# at a fraction of the cost and time of alternative approaches. For example, in a recent project we were able to convert 2.5 million lines of HP NonStopTM COBOL and SCOBOL code with 99% automated conversion in just 90 days.For more information Request a Translator demonstration
HP NonStop COBOL Translation Highlights:
Flexibility
- Freedom to choose target technologies
- Can customize translation to handle non-standard client code idioms
- No third party dependencies
- Translate multiple & mixed languages
Code Quality
- Extensive testing of translator to validate correct code translation
- Translation of COBOL names to Java or C# style names
- Translations based on in-depth code analysis
- Smart heuristics for code refactoring
- Removal of dead and redundant code
- Extraction of COPY libs as classes
Efficiency with 99+% Automation
- Shorter project timeframes, lower costs and lower risks
- No code freeze until cut over
- Translate multiple & mixed languages
Converts NonStop COBOL and SCOBOL
- Enscribe indexed files converted to relational database access according to DDL
- Option to migrate Enscribe database content to target system
- SCOBOL screens converted to HTML
Experience
- Project team of PhD. Computer Scientists
- Decades of continuing investment in DMS
- 25-year proven track record
Newsletters
Missed a Newsletter? Catch Up Here
Find out about
Tandemworld
Please Attend These HPE Shadowbase Presentations
at the NonStop TBC

If you are going to the HPE NonStop TBC event in October, please stop by Booth #P2 and attend one of our presentations. We look forward to talking with you and discussing how the HPE Shadowbase product suite can provide solutions to your most pressing business issues for business continuity, data integration and synchronization, and application integration.

Please attend HPE Shadowbase Mission Critical Use Case Solutions and Product News and learn about recent HPE Shadowbase releases and new features to solve various enterprise challenges:
· Business Continuity – maintain consistency and recoverability with active/passive, sizzling-hot-takeover, and active/active replication architectures
·
Data Integration and Synchronization – feed data warehouses, data marts, and operational data stores· Application Integration – build real-time business intelligence systems for sales, fraud detection, and more
· Zero Downtime Migration – eliminate planned application downtime, and minimize the risks associated with hardware and software changes
· Compare and Repair – ensure audit compliance and validate that the standby/target database matches the source while working alongside any replication engine
Stay tuned for more information on our second presentation, New Data Integrity Architectures for Mission Critical Systems. We will also be giving a demo on HPE Shadowbase Compare capabilities and participating in the Business Continuity Panel Discussion.
Gravic Offers Two Add-on Products to HPE Shadowbase Suite
We are pleased to offer the following add-on products to the award-winning HPE Shadowbase data replication suite of products for our HPE NonStop customers.
- HPE Shadowbase Compare is now being sold into every NonStop Business Continuity (BC) solution, regardless of the data replication product in use.

HPE Shadowbase Compare validates that the target matches the source and is how users can validate and verify that their replication configuration is correct, complete, and working properly. This link includes additional information about the benefits of HPE Shadowbase Compare (including a new, short video).
- HPE Shadowbase Essentials is now being sold into every NonStop Data and Application Integration (DI/AI) solution, regardless of the data replication product in use.

HPE Shadowbase Data and Application Integration solutions allow customers to replicate their NonStop data to and from other database and application environments, including replicating Enscribe to SQL, or between the NonStop and Other Server target databases such as Oracle, SQL Server, Sybase, DB2, SAP HANA, MySQL, Postgress, etc. The HPE Shadowbase Essentials bundle includes data transformation and mapping facilities, DDL and schema format conversion utilities, and data cleansing functions that simplify these complex tasks. Please visit this link for more information.
We are always happy and available to answer any questions you may have and discuss these add-on products with you.
Please contact us.Hewlett Packard Enterprise globally sells and supports Shadowbase solutions under the name HPE Shadowbase. For more information, please contact your local HPE Shadowbase representative or visit our website. For additional information, please view our Shadowbase solution videos: https://vimeo.com/shadowbasesoftware.
Specifications subject to change without notice. Trademarks mentioned are the property of their respective owners. Copyright 2021.
NonStop Technical Boot Camp 2021

PCI DSS 4.0 is Coming
Will you be Ready?
The next version of the Payment Card Industry Data Security Standards is scheduled for release early next year. It might be too soon to know what will change when PCI DSS Version 4.0 is released, but we can look for clues in the PCI Council’s blogs and feedback reports from industry sources who have reviewed early drafts.

Goals for PCI DSS v4.0
Based on the feedback received, PCI SSC evaluates how to evolve the standard to accommodate changes in technology, risk mitigation techniques, and the threat landscape. PCI SSC is also looking to introduce greater flexibility to support organizations using a broad range of controls and methods to meet security objectives.
These are some of the high-level goals for PCI DSS v4.0:
· Ensure the standard continues to meet the security needs of the payments industry
· Add flexibility and support of additional methodologies to achieve security
· Promote security as a continuous process
· Enhance validation methods and procedures
Key Changes to Anticipate with PCI DSS 4.0
1.
Flexibility: Customized implementation to meet the intent of security controlsThat is probably the most significant change that will come into place when PCI DSS 4.0 is released next year. The 12 requirements will shift to focus on the main security objectives reviewed in the RFCs.
The new, customized validation approach will sharply define the security outcomes linked to each requirement. With PCI DSS 4.0, organizations will have the ability to choose to perform the control as prescribed or opt for customized implementation. With customized implementation, organizations can comply by showing that they met the intent of the requirement without needing to provide an operational or technical justification.
That change will allow businesses more flexibility in modifying their implementation procedures and meeting the intent of the requirement. To verify the effectiveness, external evaluators must review the documentation and thoroughly test each control with a custom implementation.
2.
Security: More stringent requirementsThe ultimate goal of PCI DSS continues to be ensuring that all sellers safely and securely store, process, and transmit cardholder data. It is fair to assume that PCI DSS 4.0 will set the bar higher and build on the assurance of PCI-DSS v3.2.1. In addition to restructuring many of the requirements, the Summary of Changes will likely include strengthened security standards. Top management, including CISOs and CTOs, should prepare to adjust budgets to allocate capital and operational funds to implement the new requirements.
3.
Authentication: A focus on NIST Password Guidance & MFANational Institute of Standards and Technology (NIST) Password Guidance moves to the forefront in this new version. The PCI SSC places more focus on applying stronger authentication standards to payment and control process access log-ins. It has also partnered with the Europay, Mastercard, and Visa (EMVco) to implement the use of a 3DS Core Security Standard during transaction authorization.
4.
Monitoring: Technology advancement requirementsThere are likely to be more risk-based approaches in the new PCI DSS 4.0. Technology evolves rapidly, and companies are looking at pluggable options for their information systems, much like the PCI Software Security Framework. Adopting these solutions allows organizations to comply with standards while gaining faster deployment of processes without having the technology located in a specific control area.
Challenges to Consider before v4.0 is released
The core PCI DSS requirements are not expected to fundamentally change with PCI DSS v4.0, as these are still critical components of securing credit card data. However, organizations should consider the potential changes to PCI DSS requirements, as decisions that are being made now about IT infrastructure and policy could be affected by those changes.

The transition period could aggravate some challenges associated with obtaining and maintaining compliance with PCI DSS. First, there’s the threat of configuration drift. Organizations should have a goal in mind to ensure that systems in their cardholder environments remain compliant.
As always, organizations must demonstrate compliance to auditors. Time and resources must be allocated to complete the auditing process. These resources could be substantial, depending on the number of assets, tests, and controls that are in place. Organizations need to have historical data to prove compliance over time. Depending on their available resources and the size of their cardholder data environments, organizations might also find it impractical to audit all of their systems. Such a decision could prove costly if any threats remained unexposed, leaving their systems vulnerable to attacks.
Ransomware today is a billion-dollar industry. It’s crippled industries like healthcare, infrastructure, telecommunications, and finance. Hackers carry out cyberattacks at the private and public levels, and threat actors have no regard for the implications their actions have on our national and global financial security.
These attacks are possible by the ongoing presence of weak security controls and outdated operating systems. Looking ahead, it’s likely that malicious actors will continue to use ransomware to target a variety of industries. They’ll also probably go after individual organizations’ Point of Sale (POS) systems, as EMV chip cards have made data scraping nearly impossible.
One of the primary goals of PCI DSS v4.0 will be to promote security as a continuous process so that organizations can remain compliant over time.
CSP PassPort® and PCI-DSS Compliance
CSP PassPort provides important security features for NonStop servers (with or without Safeguard) and greatly expands the Guardian security package.
While Safeguard provides a range of authorization and authentication controls, additional controls are required to manage how users log onto TACL and OSH, and what privileged commands they can use. In addition to this, once a user has logged on, it is critical to control which activities they can then carry out.
 CSP
PassPort addresses some of the following PCI-DSS requirements:
CSP
PassPort addresses some of the following PCI-DSS requirements:
|
Requirement 7 |
Restrict access to cardholder data by business need-to-know |
|
Requirement 8 |
Identify and authenticate access to system components |
|
Requirement 10 |
Track and monitor all access to network resources and cardholder data |
|
Requirement 12 |
Maintain a policy that addresses information security for all personnel |
CSP PassPort
CSP PassPort provides comprehensive user and command control, password quality enforcement and auditing. It controls and filters user access to systems, programs and commands according to customized user profiles. It offers superior user authentication, command control, session control, accountability, and auditing capabilities not available with Guardian or Safeguard security.
All user terminal input/output operations (including OSS) can be monitored via an easy-to-use GUI interface, while an audit process records all user activities.
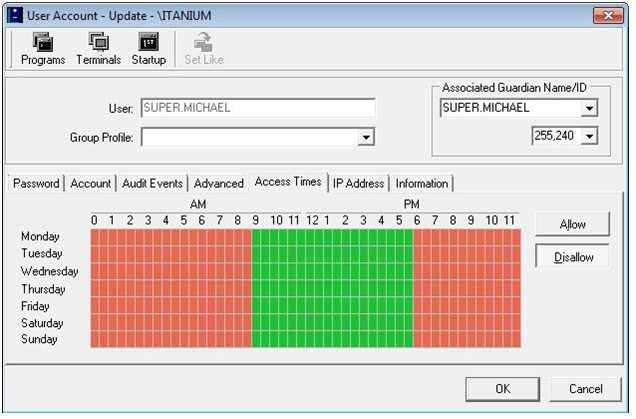
User Account Update Screen
Major Benefits:
Ø
Limit user access to sensitive assets, programs and commandsØ
Improve user accountability and audit activitiesØ
Track powerful user id’s and commandsØ Prevent easy hacks by enforcing Password Quality
Ø Eliminate the need to disclose sensitive SUPERID passwords for executing commands
Ø Generate extensive reports of user activities
Ø Get real-time notifications with Alert-Plus, and forward logs to SIEM for analysis
Key Features:
Ø
Monitor and audit user sessions down to keystroke levelØ
Role-based user accessØ Time restrictions by command and program
Ø User Authentication SEEP to prevent users from logging on outside CSP PassPort
Ø Powerful Custom Reporting
Ø Control client connections by IP address or IP address ranges
Ø Multi-factor authentication support (coming soon!)
Learn more about CSP PassPort here.
CSP - Compliance at your Fingertips®
For complimentary access to CSP-Wiki®, an extensive repository of NonStop security knowledge and best practices, please visit wiki.cspsecurity.com
We Built the Wiki for NonStop Security ®
 +1(905)
568 –8900
+1(905)
568 –8900
A new TANGO Benchmark on HPE NonStop

In 2012, Lusis Payments conducted a historic proof of concept with partner HPE at the HP ATC (advanced technical center) in Palo Alto, CA. TANGO was tested for 48 hours straight at full capacity. The system processed 2,500 TPS without fail. The hardware configuration used at the time of the benchmark was chosen to match a client’s production system and consisted of a 8-processor HPE J-series NonStop. TANGO proved responsive and surpassed normal daily tasks and nightly settlements. This proof of concept proved that TANGO was fault tolerant and achieved maximum volumes and throughput of a total daily volume of 50 million transactions per day.
The outstanding results came from long hard-working sessions with the HPE teams which we were proud to work with. The first week included our CTO working on-site. Soon after, he was joined by our senior project leaders, and they received significant additional support from our lab in Paris. In addition to the dedicated HPE team, the client’s team also partnered with us to test the conformity of the benchmark protocol. HPE worked with the client to reproduce its environment for a true simulation. It was great project, and we were proud of the outcome.
Since then, HPE has continued to suggest that we test TANGO on the newest (Intel based chip) hardware. As we were still quite pleased with the 2500TPS results and the fact that the client continued to realize improved performance on their HPE NonStop platform, we chose not to do additional test campaigns in subsequent years.
Until now.
At the end of Q1 we said “ok, let’s do it”! At that time, bandwidth was quite low, so we made it “our dry way of doing it.” We used our Vanilla switch based on the TANGO version 7 platform installed on HPE NS server: 8 processor, 6 core NS7-X3 system again at the HP ATC labs. This system runs OS release L21.06.17.2 with NonStop SQL/MX 3.7.2. Each NonStop processor contained 256 GB of memory. We used a very similar testing protocol without any specific tunning. And “Torpedo… LOS”!
On our first run we achieved 3,500 TPS. Then with less than 10 hours of tuning, we easily reached 4,500 TPS sustained for two straight hours.
So, this has become our new reference on HPE NonStop:
4,500 transactions per second on an 8-CPU machine.
And this was simply done with our Vanilla switch and some very light tuning. So, nothing heroic, just the standard product using a standard configuration.
In Q3, we will test TANGO with the new Posix Kernel of HPE NonStop and see where we take it!
Stay tuned.
Philippe Préval Lusis
CEO Chez Lusis
Learn more about TANGO the complete Payments Solution by visiting www.lusispayments.com/tango.
Brian Miller
General Manager
Lusis Payments
www.lusispayments.com
Ask TandemWorld
Got a question about NonStop ? ASK Tandemworld
Keep up with us on
Twitter @tandemworld
We are currently seeking skilled resources across the EMEA region,
contact us for More Info
www.tandemworld.net
XYPRO and HPE Partner to Provide ZERO Trust Security for HPE NonStop
A recent industry phishing report showed that 4% of users are prone to click on anything sent to them. That is a scary statistic given that phishing is one of the primary methods ransomware attacks are carried out. Ransomware is extremely damaging for a business due to its relatively low cost to execute and high value rate of return. Four percent might seem like a low number, but just one user falling victim to a phishing attempt is one too many. We, as cybersecurity professionals, need to be right 100% of the time, whereas the attacker only has to be right once. With 4% of users clicking on just about anything and opening attachments, the odds are definitely stacked against us.
Another alarming consideration: 24% of data breaches are still due to a malicious insider. This could be an employee, a contractor or some other trusted entity with access to your systems and data for legitimate business purposes, but in fact is misusing the level of access they have been granted.
The Traditional Model - Trust But Verify
We are all used to the traditional security model where we authenticate ourselves to an application or perimeter device - such as a VPN - then continue on carrying out our responsibilities.
This model assumes everything inside an organization’s network is trusted, so once a user is authenticated to the VPN, they can move around to any resource to which they have access. The assumption is made that the user is who they say they are, the user’s account is not compromised and that the user will act responsibly.
The accelerating Growth of “Buy Now Pay Later”
As OmniPayments prepares to greet customers at the Denver TBC event, there’s one payments theme which is attracting increasing attention.

I’m revisiting the topic of Buy Now Pay Later (BNPL) because it is gaining an increased amount of consumer and investor traction. And it appears to be gaining it at the expense of Credit Card Issuers. One of the things people like least is the removal of a safety blanket when you need it most. However this is exactly the pattern that we saw at the start of the pandemic. Credit Card issuers starting writing to their customers, either to reduce their credit amounts, or to cancel their credit cards altogether. Add to that the tendency of Gen”Z”ers to question the very existence of banks and financial providers, the difficulty of applying for credit cards, and you end up with a ripe market for BNPL. Something like 1 in 20 purchase transactions online is now one where the consumer elects to pay with BNPL. As for banks, well they’ve just become just another phone app amongst many others. Highly regulated with high capital requirements and oversight, they struggle to innovate.
The BNPL players in this market are numerous: US-based Affirm, Sweden-based Klarna, PayPal who launched their product only last year, and AfterPay in Australia, which was recently acquired by US-based Square for some $29bn. Major credit card companies such as Visa and Mastercard have also incorporated BNPL offerings.
It seems a no-brainer for Retailers and Merchants too. The payment method increases customer spend, boosts the goods dropped into carts, and also improves repeat business, according to the recent PayPal release. Merchants are generally paid in the same time-frame as a standard purchase.
It gets better for consumers too, especially in those parts of the world where Late-fees have until now been imposed.
Given that consumers can be tempted into buying products they may not be able to afford, this growth in BNPL has already come to the attention of regulators. In the United Kingdom, the government has been considering how the Financial Conduct Authority might regulate BNPL payment services.
Sitting behind these BNPL choices are technologies such as OmniPayments OmniCloudX solution. Consumers want choice of payment options and OmniPayments is delivering it through its cloud-based solution. Merchants who want to manage their own payment choices can now deploy Buy-Now-Pay-Later with OmniPayments.

BNPL requires the dynamism of a true real time card processing system, one that can both create a virtual card record entry in real time, capture enough of the customer’s details and associate that purchase with that same card record, and be ready to generate communication with the clients to remind of the due payment and options for payment.
OmniPayments provide BNPL as part of its Card Management, Authorisation, Loyalty, and Fraud Management Portfolio.

For more information on how we can help you integrate Buy Now Pay Later services into your internet payment gateway, please see our illuminating YouTube videos (https://www.youtube.com/watch?v=jHioqS1ZXOA), follow us on Twitter “@omnipayments” or visit www.OmniPayments.com for further information.
NuWaves API Security Guide - Best Practices for REST Services

REST has become the standard for information exchanged between disparate platforms and applications within the enterprise. In the NonStop space it is being used more and more, to allow NonStop applications to communicate with other enterprise applications, and integrate with solutions outside the enterprise. In these environments security is critical. In this article we explain some of the best practices to consider to help protect your sensitive data and applications, while still making them easily accessible to your internal and external business partners that require access. We’ll also give some real-world examples showing how LightWave ServerTM and LightWave ClientTM users are doing exactly that.
When implementing a secure REST services strategy, one must consider the following items as part of your best practices.
- Network isolation
- Protection of sensitive data in transit and at rest
- Authentication
- Authorization
- Access control
- Auditing
We will elaborate on these best practices, with a goal of assisting those interested in deploying secure REST services. Not all of these security points will be required in every instance, but all should be considered. Specific organizations may have additional requirements that should be discussed with the organization's security team.
Read the complete article here
TANDsoft’s FS Backup and Restore – Say Goodbye to Whole File Backup
Whole Files Backed Up On Day One, Then Only Changed Data Blocks Within Files Backed Up Moving Forward
Whether a company backs up data on a daily, weekly, or monthly basis, FS Backup detects file data-block modifications and archives only the changes. Redundant data is not archived. FS Restore then retrieves and applies the modifications to rebuild the original file. The product is popular with HPE NonStop customers whose hours-long backups are creating challenges within their processing environments. FS Backup and Restore does not replace HPE NonStop Backup and Restore utilities. It complements them as well as all other third-party physical and virtual NonStop tape products and storage solutions.
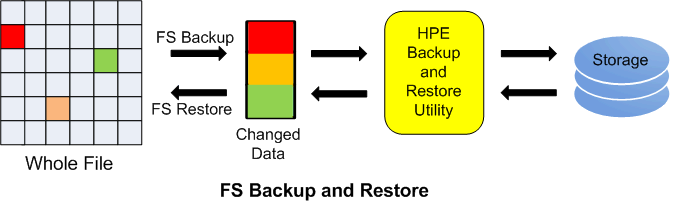
Reduces backup times from hours to minutes by backing up and restoring data block differences, not whole files
FS Backup and Restore Backs Up To Disc, Then Optionally to Tape
Unlike the commonly used methodology of backing up directly to tape or virtual tape, FS Backup and Restore backs up to disc, then optionally (based on a customer’s preference) to physical or virtual tape for safekeeping. Since changes only are backed up, far less storage is required. A month’s worth of dailies and more can be backed up easily to disc. This allows for tremendous efficiencies not only in storage requirements but also in backup time. From hours to minutes.
FS Backup and Restore Features and Benefits
- Incorporates block hash compare and source-deduplication technology
- Backs up and restores data block differences, not whole files
- Can be used to improve backup times for TMF Online Dumps and Recover Files
processing
- Complements HPE NonStop backup and restore utilities
- Supports all Enscribe, OSS, SQL/MP and SQL/MX files
- Incorporates wildcarding and qualified expressions
- Supports multiple concurrent users
- Supports fault tolerance and parallel processing
- Significantly reduces backup times for weekly and monthly backups
- Certified on all HPE NonStop servers
- Zero application modifications required
- Complements all NonStop and third-party physical and virtual tape storage solutions
- Easy to install, Easy to use
- Free trials are available
- Reports – current and historical statistics are available
- Automatic or scheduled file backups
Learn more about any or all TANDsoft products by contacting Jack Di Giacomo (+1 514-695-2234 / jack.digiacomo@tandsoft.com) or Dieter Orlowski (+1 303-263-4381 / dieter.orlowski@tandsoft.com).
TANDsoft Will Exhibit at the In-Person Boot Camp and in the Virtual Boot Camp
We can’t wait to see you this October, either in-person or online. TANDsoft will exhibit both new products and flagship products at the NonStop Technical Boot Camp in Denver, Colorado USA from October 5th through October 7th. We are Booth S10. TANDsoft also will demo a new and exciting product on Tuesday, October 5th. Drop by the Boot Camp demo area to learn more about “Accessing SQL/MX Data from Enscribe Applications, Transparent to the Application, and Blazing Fast.”
Can’t make it to Denver? Visit TANDsoft’s virtual booth at the TBC21 Digital Experience event. It opens online on October 13th. For more information and to register for either event. https://www.nonstoptbc.com
Since 1993, TANDsoft has served as a global provider of innovative HPE NonStop software solutions for use in time virtualization, application modernization, security, and business continuity. Many NonStop customers use our intercept technology to enhance application functionality with no program modifications or even in the absence of source code. Check us out at www.tandsoft.com for updates on all our products. In addition to FS Backup and Restore, our portfolio includes the new FS Compare and Repair, our flagship products FileSync and OPTA2000, Sensitive Data Intercept for security and compliance, the Enscribe-to-SQL Toolkit for application modernization, and the OPTA suite of application tools.
XYPRO to Present at HPE NonStop Technical Bootcamp 2021
XYPRO is proud to announce our participation as a Gold Sponsor at the HPE NonStop Technical Boot Camp 2021. This year’s program will feature both live, on-site activities, hands on demos, training as well as virtual programs. The 2021 NonStop TBC will be held in Denver, Colorado on October 5-7.
HPE and XYPRO will be providing a pre-conference education session on XYPRO’s flagship XYGATE SecurityOne™ Security Analytics software. Described as “A single pane of glass to monitor security across your system”, this 4-hour training session will provide an in-depth look at utilizing SecurityOne to protect your NonStop environment.
As an HPE Partner expert, XYPRO’s Chief Product Officer and CISO, Steve Tcherchian will provide his expertise as part of the event’s Security Panel Discussion on Tuesday, October 5th.
The Boot Camp event will be recorded and registrants will have access to a large on-demand library where users can play or replay talks at their leisure.
For more information, and to register, visit https://www.nonstoptbc.com/
Migration Services

Find out more about us at
www.tandemworld.net
+44 (0) 20 8304 7979
Our company, Tandemworld,
accepts no liability for the content of this email, or for the
consequences of any actions
or information provided.
To Unsubscribe or Change your Subscription Please click here