| |
|
Are
the systems you’ve relied upon for years still fit for purpose?

I ask this this questions with a fair degree of
concern.
Just this week, the notable security journalist
Brian Krebs highlights the FBI warning to the Banking Industry of a
potential impending “Cash-Out” across the world.
They foresee a replay of the heist of a few years
ago when a Card Issuers’ systems were hacked, daily limits raised, and
then agents across the middle east withdrew some US$45 million within
several hours. Not until the heist was over did anyone really notice
this unusual activity. No-one smelled a rat till the rat had scurried
away, melting into the night.
So many of the systems we reply upon today still
date from before the days of the Internet, before the days of the iPhone,
and certainly before the days when the words Dark Web and Hackers
drifted into modern use. Since that time, we’ve been busy trying to
adapt our old systems for the modern world, tacking on bits of software
here and there, plugging this gap and that gap, changing a few
operational procedures, jumping through a few hoops to satisfy the
regulators. But what continues to happen? Fraud keeps on rising, and
the Fraudsters have increased incentives to carry on increasing their
line of business.
OmniPayments takes a 21st century
approach to payments. We recognise that modern systems require a number
of key characteristics:
·
Flexible APIs
·
Rapid implementation times
·
Robust Security
·
Active/Active built-in
Read
more
Make MQ Work Harder
Early and current releases of IBM MQ for NonStop
are subject to the following information being placed into a single text
token:
●
Error condition
●
Cause, Effect, Recovery
●
MQ Manager
●
MQ Channel
●
MQ Queue
Ordinarily, the diagnostic information should be
held within the Event buffer as a set of discrete tokens. In the earlier
releases of MQ, this was the case but in subsequent versions relevant
information has become embedded in large text tokens.
This approach makes the error messages difficult to
retrieve, process and escalate.
Imagine several MQ EMS events being issued to your
event viewer - how do you tell which is ‘good’ or which is ‘bad’? The
same IBM.MQ.5, event number 00005 could be issued for a variety of
‘good’ & ‘bad’ conditions.
Take control of your MQ Events
MQ Gate from Insider Technologies provides a
solution where it obtains the source MQ events including its lengthy
text value, parses them and creates new, unique tokenised EMS events.
It’s easy to use, and purpose built to enable
NonStop administrators to improve visibility of their environment:
• Extract the IBM MQ error number from the source
event, e.g. AMQ9512
• Extract any other required attributes such as
Channel, Queue
• Generate a new, fully tokenised EMS event
MQ Gate utilises source attributes and generates
them as discrete tokens within the new event:
●
Event number
●
MQ Manager
●
MQ Queue
●
MQ Channel
●
MQ Process
●
Event text
●
Subject token
How does it work?
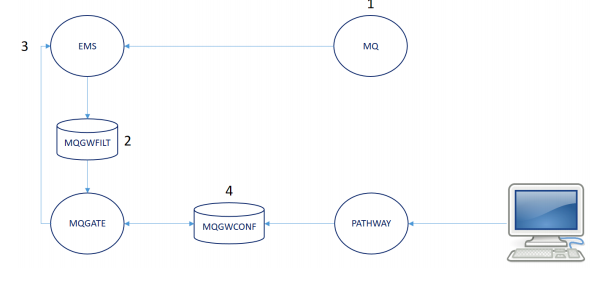
-
IBM MQ issues events to an EMS
collector.
-
The MQGATE program utilises a
compiled MQGWFILT filter to retrieve nominated source IBM MQ EMS
event and associated text from the EMS collector.
-
Based on the content of the
configuration file - MQGWCONF - the MQGATE process will create and
issue a second event in $0. This event will have a unique event
number and in addition any attribute names will be extracted from
the body of the text and included in the new event as discrete
tokens, e.g. a Subject Token containing the name of the MQ Queue.
-
Deciding on which events to
process and whether any new tokens are added, is performed within
the MQGWCONF file. A Pathway interface is provided to help maintain
this database.
Get the benefits now!
Now that unique, tokenised EMS events are being
issued for MQ via the use of MQ Gate, users can monitor just the
specific events they are interested in.
For example, instead of monitoring all the same
IBM.99.0, event 5 events and having to scroll through an event viewer
such as ViewPoint to review the event text as to what the event is
referring to, the unique EMS event structure as generated by MQ Gate
allows a user to filter their monitoring software on selected event
numbers and/or subject tokens, e.g.
●
SSID - INSIDER.MQEMSG.5
●
EVENT NUMBER – 8016
●
SUBJECT – MQ Channel Name, e.g.
INSIDER.TO.LONDON
●
EVENT TEXT – ‘WebSphere MQ Channel Changed’
Exception alerting is an immediate benefit of MQ
Gate, as based on the above, you can specify which events you are
interested in. Otherwise, a user needs to monitor ALL IBM.99.0, event 5
events and by doing so, will find it slow and difficult to determine
which of these MQ events are a cause for concern.
The product arrives pre-configured with a wide
range of converted events and when installed, MQ Gate is actively
monitoring the EMS collector for any IBM MQ events.
You can follow Insider Technologies on
Twitter @insidertech, on LinkedIn, or get in touch via hello@insidertech.co.uk
Karl Gilbank | Sales & Marketing Director
+44 161 868 6658
www.insidertech.co.uk
Switching
Replication Engines with Zero Downtime – Part 2
Gravic recently published
Part 2 of the article series, Switching Replication Engines with
Zero Downtime in the July/August issue of The Connection.
Sometimes it is necessary to change or upgrade to a new data replication
engine version. The zero downtime migration approach will impose no
downtime on either applications or users. This migration technique is
similar to the HPE Shadowbase Zero Downtime Migration (ZDM) technique
that customers have been using for decades to upgrade their
applications, database schema formats, file and table locations (or
indices), operating systems, or perform a hardware refresh. This article
discusses how the Version Independence approach discussed in
Part 1
of this series can be improved using one or two
additional nodes. It also explains how to protect the old production and
old standby system(s) while the replication engines are being upgraded
or switched.
Gravic Publishes New HPE Shadowbase Presentation Web Page
Gravic
published a new
Presentation web
page on its Publication website pages, featuring the latest HPE
Shadowbase data replication software solutions. We hope that you enjoy
learning more about these solutions, product updates, use cases, and
case study from viewing the following presentations:
·
Overview and Use Case Solutions
·
Competitive Positioning and Value
Proposition, BASE24™, and New & Future Features
·
Support for IBM DB2
·
Delivering Business Continuity for
Vital Applications – Best Practices (an
HPE presentation)
·
Prescription Drug Fraud Prevention –
Data Integration Case Study
To speak with us about your
data replication and data integration needs, please call us at
+1.610.647.6250, or email us at
SBProductManagement@gravic.com.
Hewlett Packard Enterprise
directly sells and supports Shadowbase solutions under the name HPE
Shadowbase. For more information, please contact your local HPE
Shadowbase representative or
visit our website
Please
Visit Gravic at these Upcoming Events
|
OZTUG HPE Technical Summit—Sydney
& Melbourne, 18 & 20 September |
|
ATUG Meeting—Atlanta,
19 September |
|
CTUG Conference—Toronto,
26-27 September |
|
MATUG Meeting—Baltimore,
28 September |
|
MEXTUG Meeting—Mexico
City, 4 October |
|
Connect HPE Technical Boot Camp—San
Francisco, 11-14 November |
|
SunTUG Sunshine Summit—Tampa,
1 March, 2019 |
|
EBITUG—Edinburgh,
14-15 May, 2019 |
Using Multi-Factor Authentication to
Solve Compliance Requirements on Nonstop
What is Multi-Factor Authentication?
Multi-factor authentication (MFA) is a security
measure that requires two or more methods of authentication, from
independent categories of credentials, to verify a user's identity for a
login or other transaction.
In
other words, multi-factor authentication verifies that the person
attempting to perform a transaction is who they say they are, by
requiring two or more pieces of evidence (factors) to an authentication
request.
These factors can be categorized into the following:
·
Knowledge
- Something only the user knows, e.g. password
·
Possession
- Something only the user has, e.g. token
·
Inherence
- Something only the user is, e.g. fingerprint/biometrics
The authentication mechanisms used for MFA should be
independent of one another such that access to one factor does not grant
access to any other factor, and the compromise of any one factor does
not affect the integrity or confidentiality of any other factor.
What does PCI say about Multi-Factor
Authentication?
One of the key changes to PCI DSS is an update to
requirement 8.3, which now calls for organizations to strengthen their
access security with MFA instead of the previously stated two-factor
authentication. By changing the terminology of requirement 8.3, two
forms of authentication are now the minimum requirement.
As detailed in PCI DSS version 3.2, any individuals
with non-console administrative access to Cardholder Data Environment (CDE)
must authenticate using MFA. “Non-console administrative access” means
that the system is accessed over a network, as opposed to the system’s
local screen and keyboard. This applies regardless of whether the
individual is an employee or third-party IT support personnel.
An Exciting New Solution for MFA: CSP
Authenticator+
Multi-Factor authentication has become vital in
ensuring secure access to systems. The new
CSP Authenticator+ provides a RESTful
interface to support multi-factor authenticated logins to NonStop
systems.
CSP Authenticator+ can be used as a Safeguard
Authentication SEEP or with Pathway and Non-Pathway applications.
Methods supported include RSA SecurID, Email, Text Message, Google
Authenticate and Radius. Many additional methods are planned for the
future.
CSP Authenticator+ resides on the NonStop Platform
and uses an OSS “bridge” to connect via a RESTful interface to the CSP
MFA service. Almost any application, including TACL, can now easily
support Multi-factor authentication.
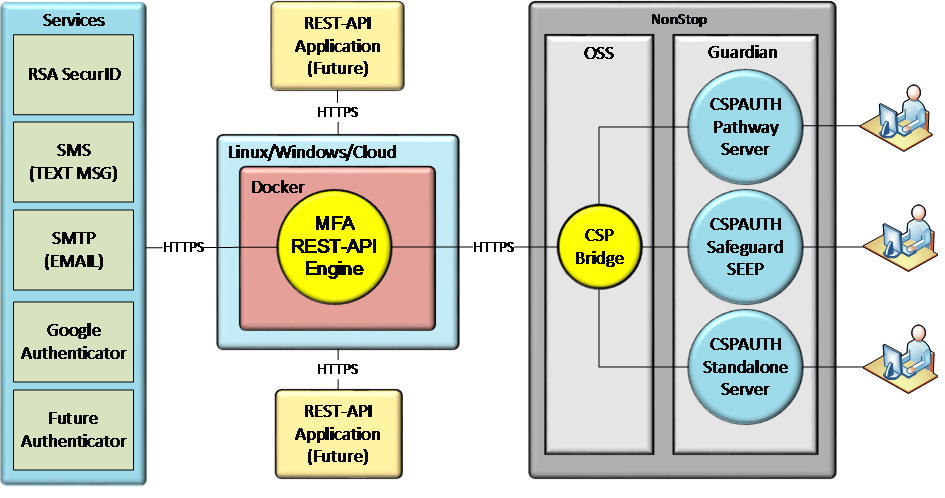
Key features include:
·
Support for multiple authentication
factors, including SecurID (RSA) tokens
·
Standardized authentication across
platforms
·
Configurable for all or selected users
·
Certified for the latest RSA release
·
Support for virtual addressing
For more information on CSP solutions visit
www.cspsecurity.com
For complimentary access to CSP-Wiki®, an
extensive repository of NonStop security knowledge and best practices,
please visit
wiki.cspsecurity.com
We Built the Wiki for NonStop Security
®
Visit us at these upcoming shows to learn more about
our exciting solutions for NonStop and beyond:
ATUG - Atlanta, GA
September 19, 2018
CTUG - Toronto, Canada
September 26, 2018
MexTUG - Mexico City, Mexico
October 4, 2018
Regards,
The CSP
Team
+1(905) 568 - 8900
Connect
with NuWave at NonStop Events Around the World
We had an amazing time
connecting with many of our customers, partners, and friends this spring
and summer. You can check out our recap
of the spring NonStop events to read up on some of our favorite
conferences, including SunTUG, BCD in India, SCTUG, BITUG Big SIG, the
European NonStop HotSpot, NENUG, and NYTUG. Take a look at our
slideshows of BITUG
and the European NonStop HotSpot and the NonStop
spring and summer events on YouTube!

Andrew Price and Friends at BCD India
We are keeping very busy
this year, and we're already looking forward to the upcoming shows this
fall. We would love to see you, so please reach
out to us if you are planning to attend OZTUG
Sydney or OZTUG Melbourne in
September, or NonStop Technical Boot Camp (TBC)
in November. In North America, you can also connect with our US and
Canada reseller, TIC
Software, at ATUG, CTUG, and MATUG in September, as well as at Boot
Camp. We hope to see you soon!
TW & B24
Base24 user ? Low on resources , need some short
or longer term assistance with projects ?
Tandemworld have a number of highly skilled Base24
specialists that can assists you immediately within the EMEA region.
We can provide you with 1 specialist or a team of
specialists to Augment your IT Service..
Tell us where your pain is or what you are looking
to achieve, we can help with the right specialist(s).
Contact us at
B24@tandemworld.net
NEW SECURITY REQUIREMENTS
FOR ATM AND POS INTRODUCED BY PCI-PIN V3: TR-31 and TR-34
Lusis
Payments is committed to providing our clients with helpful information
to remain ahead of the curve on topics such as new compliance
requirements or guidelines in the payments industry. The following is a
brief summary of the new security requirements that were introduced by
PCI-PIN V3 that merges requirements from the PCI Security Standards
Council (PCI SCC) and the Accredited Standards Committee X9 Inc (ASC X9)
to create one unified PIN Security Standard for payments stakeholders.
There are two evolutions that have emerged from the standards that will
introduce a massive change in ATM and POS remote key management. They
are ASC X9 TR-31 and TR-34.
X9
TR-31
TR-31 is a Technical Report. Technical Reports are different from
standards, which are mandatory sets of rules that must be adhered to.
Technical Reports are not mandatory but do provide guidance to those who
are implementing the standards. TR-31 is a method that is consistent
with the requirements of the ANS X9.24-1 standard for the secure
exchange of keys and other sensitive data between two devices that share
a symmetric key exchange. No other specific methods have been defined by
the standards committee, therefore the TR-31 method has become the
adopted standard through which financial organizations will exchange
keys. The TR-31 key block has a set of defined key rules.
Click
HERE to Read the full article.
Brian
Miller
Lusis Payments, North America
(415)
829-4577
Brian.Miller@lusispayments.com
Secure Application
Development in a Connected World

Applications are everywhere. Take a look at your mobile device and you
will realize how integral applications are to everyday life. We use them
to shop, bank, order dinner, get a ride, keep our house warm, even keep
track of our children. But such modern conveniences do not come cheap.
Our data needs to be shared with applications for them to provide value.
In most cases, extremely sensitive information about us and our lives.
Who we are, where we live, where our kids go to school, our daily
patterns, habits, likes and dislikes. All this data is shared under the
assumption and hope that the application creator is doing everything
possible to protect our most personal information. As the Facebook/Cambridge
Analytica scandal proved, that is hardly the case. Even more disturbing,
that information was shared with Facebook’s knowledge. (Read
more about Cambridge Analytica here. )
According to the 2018 version of Verizon’s Data Breach Investigations
Report (DBIR), applications were the top attack vector when it came to
information data breaches, exponentially surpassing common attacks such
as backdoors or command and control (C2) vectors, even insider attacks.
Why are Applications a Target?
Most applications need data to provide value. YOUR data.
A recent ZDNet article mentioned “Researchers at security firm Positive
Technologies,
tested 33 websites and services using its proprietary application
inspector and found that banking and financial institutions were “the
most vulnerable” to getting hacked.”
Why? Because most applications are horribly insecure and developers do
not follow security best practices when developing an
application. Applications are designed for functionality, not security.
Security is difficult and time-consuming, often adding delays to product
launch and revenue generating activities
Learn how to protect your application development process – read more
GDPR & TW
GDPR: On 25th
May 2018, a new European Union (EU) data protection law, the General
Data Protection Regulation (GDPR), takes effect. The GDPR gives
individuals in the EU more control over how their data is used and
places certain obligations on businesses that process information of
those individuals. We are updating our Policy to take into account the
new requirements of the GDPR.
In accordance with this we
need your permission to continue to send you emails relating to the
Nonstop World (Tandemworld) Limited eNewsletter and the products and
services that you can purchase from Nonstop World (Tandemworld) Limited
Preferences
It is extremely important
that you update your preferences with us, to comply with the new GDPR
regulations – simply click one of the following links, to confirm your
mailing preferences.
The only data we collect
and hold is your email address. We collect no further information.
CONTINUE
New
NonStop Innovations Blog Articles
A US-based
finance company decided to ditch their previous solution and connect to
their payment application using NuWave middleware. By switching out
their integration software, this innovative HPE NonStop customer saved
approximately hundreds of thousands of dollars, and the savings continue
to grow each year.
Read more
about the
payment innovators.
One of NuWave's
customers recently implemented an interesting use case with LightWave
ClientTM.
This customer processes payment transactions, and as part of the
transaction authorization process, needed to integrate with a REST-based
rules engine running on Unix. HPE NonStop users all over the world are
using REST APIs to allow their customers to do exciting new things with
mobile, browsers, IoT, and more.
Learn more
about how
NonStop customers are using REST to up their game.
Storage
Director Use Cases from Tributary Systems
By Glenn Garrahan, Director HPE Business, Tributary
Systems
When
to use Storage Director
Regular readers of Tandemworld are well aware of Tributary Systems’
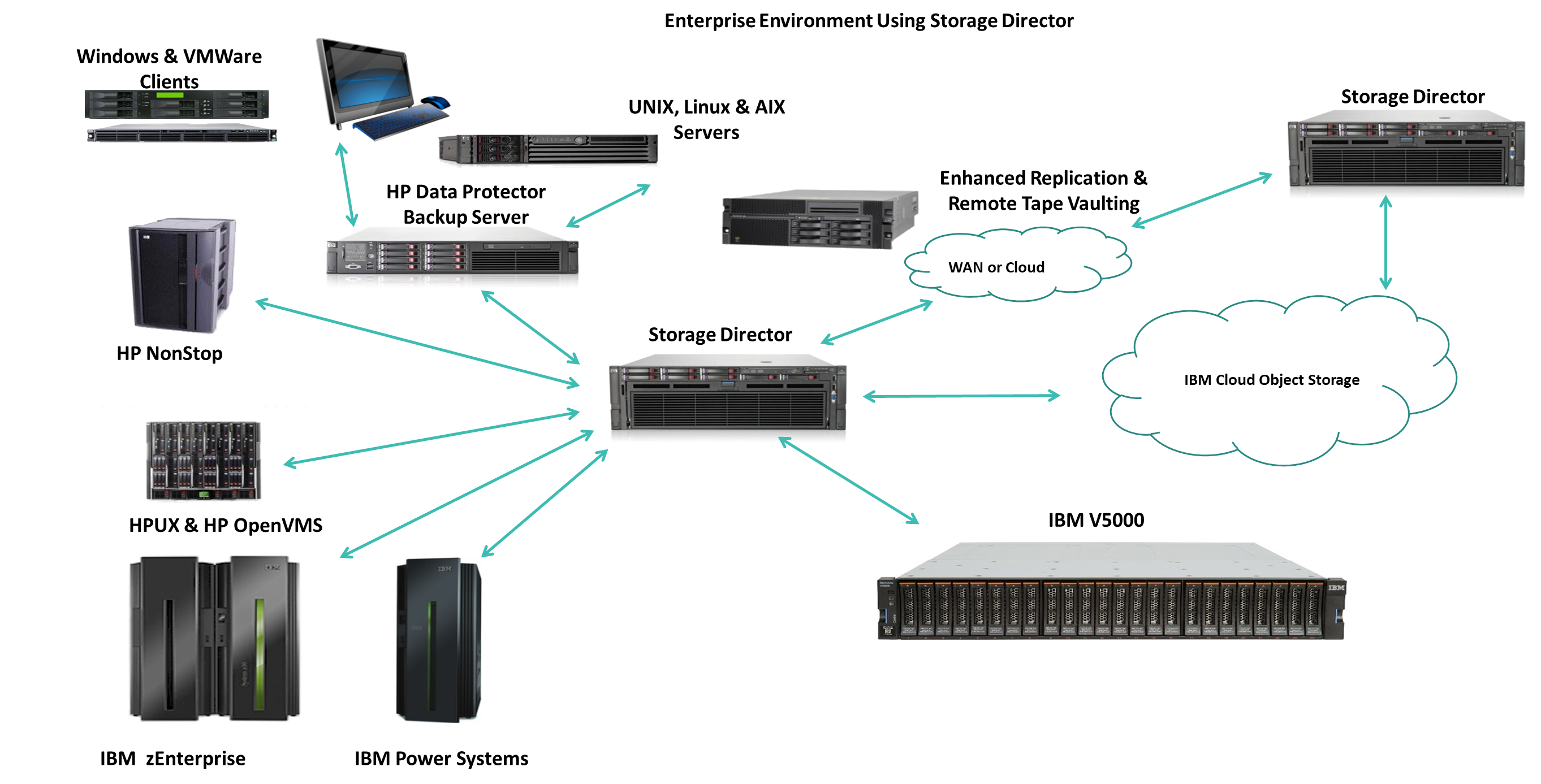
flagship product Storage Director. Put succinctly, Storage Director is a
software defined, policy-based and tiered enterprise backup
virtualization solution that enables data from any host, OS or backup
application, to be backed up to any storage device, media or technology,
including IBM’s Cloud Object Storage (Cleversafe) platform, or any S3
compatible cloud. Storage Director is a fully virtualized target for
any backup application such as Spectrum Protect, NetBackup, Commvault,
Veeam, etc. and enables policy-based data pools to be created and backed
up to multiple targets and replicated for remote storage and DR. Storage
Director is unique in being able to present a single backup target or
solution for backing up all open environments, such as Linux, Windows,
VMWare, UNIX, etc. as well as all proprietary host platforms, such as
IBM Mainframe (z/OS), iSeries, HPE NonStop, HP Open VMS etc. on a single
node.
Storage Director has an
optimized backend S3 interface to allow customers to stream their data
post backup process to IBM’s Cloud Object Storage enterprise backup and
archive platform or any S3 public cloud target. Storage Director can
backup and restore data to any S3 cloud target using large block sizes
as well as a function called DRestore™ which restores large amounts of
data in disaster recovery situations.
Specific Use Cases
Check
out the use cases detailed below, see if your backup/restore needs don’t
fit into one of them. We’re betting they do:
Backup/restore with
proprietary dedup storage
•
PROBLEM: Not cost
effective, doesn’t scale efficiently, slow restores due to data
re-hydration, expensive proprietary hardware
•
SOLUTION: TSI
Storage Director with IBM COS- reduces costs by reducing required disk
space, eliminates re-hydration issue during restore because data is
never deduped, only compressed, Storage Director/ICOS solution uses
off-the-shelf non-proprietary hardware
•
BENEFITS: In an
average 3 site configuration, the Storage Director/ICOS solution uses
35% to 65% less disk space than the typical dedup solution. Performance
is enhanced because data is not manipulated on the front end nor is it
re-hydrated during a restore
Backup to Tape
•
PROBLEM: Handling and storage of large numbers of tape cartridges is
inefficient.
•
SOLUTION: TSI Storage Director with ICOS- Storage Director is an easy to
install, easy to use policy based solution that emulates tape. Backup
applications do not need to be modified, Storage Director interfaces
with most every popular BMA in use today, from a user point of view it’s
a transparent upgrade.
•
BENEFITS: Eliminate inefficient tape handling by IT staff, no need to
manually transport tape cartridges offsite for secure storage, removes
concern for data degradation on very old tape, data restores are much
faster because cartridges don’t have to be located and physically
mounted
Public
Cloud Backup
•
PROBLEM: Public
Cloud providers don’t offer users control of their data, charges for
puts and gets, data security concerns
•
SOLUTION: TSI
Storage Director with ICOS- Allows use of on-premise private cloud with
fixed costs
•
BENEFITS: On-premise
private cloud eliminates security concerns associated with public cloud,
variable costs with puts and gets replaced by lower fixed cost for
backups, data ingestion and restore performance is significantly
improved when compared to a public cloud
If you’d like additional information on Storage Director, visit
www.tributary.com,
or call Matt Allen at 817-786-3066 (office) or 713-492-7434 (cell).
Storage Director allows
NonStop professionals to “augment what they have and use it in creative
new ways!”
Registration Now
Open for the MATUG Fall Users Meeting

Please
register via EventBrite
for the Mid-Atlantic Tandem User Group (MATUG) meeting scheduled for
8am-5pm on Friday, September 28, 2018 at the
DoubleTree by Hilton Hotel Baltimore-BWI Airport
near Baltimore, MD, USA. (Click
https://eventbrite.com/event/16902004350/
for more information.) Expect HPE presentations on the NonStop HW/SW
product roadmap and new technology with blockchain, as well as several
informative vendor presentations.
Calling all VENDORS, ISV’s, and SOFTWARE PROVIDERS: There are only two
25-minute vendor presentation slots still available, for a reasonable
sponsorship fee (TBD based on overall meeting expenses, including meals
and estimated to be around $500). These slots will be filled on a
“first-come first-serve” basis, based on the time of your email response
to
Susan Loeliger,
MATUG Secretary/Treasurer. (User presentations take preference and are
free.)
To assist with travel plans, please note that the CTUG Fall Conference
will be held two days prior to MATUG on Wednesday, September 26 in
Mississauga, Ontario.
The MATUG meeting is open to
all HPE NonStop customers, partners, users, consultants, or interested
parties. Members are usually from the following states: Pennsylvania,
New Jersey, Maryland, Delaware, Virginia, Washington, D.C., and West
Virginia, although anyone can attend. MATUG provides members with the
opportunity to participate in quality informational sessions, learn
about new HPE products and services, and interact with fellow HPE
NonStop users.
Please forward this announcement to others in your organization who may
be interested in attending.
|
 |
|
On behalf
of the NonStop Partner Community - We look forward to
seeing you at the NonStop Technical Boot Camp!
22 Vendors Exhibiting:
|
4tech
Software |
ACI |
|
Ascert |
BlackWood Systems |
|
comForte |
Crystal
Point |
|
Computer
Security Products |
ETI-NET |
|
FSS |
Gravic |
|
Idelji |
IR |
|
Lusis |
Network
Technologies |
|
NuWave |
OmniPayments |
|
TANDsoft |
TCM |
|
TIC |
Tributary Systems |
|
XYPRO |
Hewlett
Packard Enterprise |
|
|
|
See you soon!
Kathy Wood
NonStop Partner SIG/Vendor Chair
kwood@blackwood-systems.com
Example Breakout Sessions:
-
It’s the Hardware! It’s the Software!
-
Virtualized NonStop (vNonStop) and VMWare
-
Blockchain done on Ethereum; connected to NonStop
-
Increasing Availability with the OmniPayments Hub
and HPE NSX
-
Innovation: CCA Modernizes the Person to Person
Real-Time Payments
-
Recovering a DR site using Shadowbase tricks
-
A day in the life of a NonStop professional
|
 |
SAVE $300 NOW WITH EARLY BIRD REGISTRATION
Take advantage of early bird savings until
October 1, 2018.
Register NOW for just $1395. |
|
 |
RESERVE YOUR ROOM AT THE HYATT REGENCY SFO
Connect has secured a great room rate for Boot
Campers at the Hyatt Regency San Francisco
Airport. Reserve your room before
October 22, 2018 to get the
Group Rate of
$209 per night.
Reserve your room online now.
|
|
 |
CALL FOR PAPERS IS OPEN
Do you have a technical breakout session you
would like to present at boot camp? Share your
NonStop solutions and technical knowledge at
this year's #NonStopTBC. The deadline to submit
your session is
September 1st.
Learn how to submit your session here. |
|
NEW IN 2018:
WOMEN IN TECHNOLOGY MIXER
Join the Women of NonStop for a special mixer on
Monday, November 12th at 5:30pm.
Hear more about the Future Leaders in Technology
Scholarship program and network with the women
who power the NonStop community.

|
|
NEW IN 2018:
NONSTOP UNDER 40 PUB CRAWL
Are you NonStop Under 40 (NSU40)? If so, don't
miss out on the first annual NonStop TBC Under
40 Pub Crawl! Stay tuned for details!

|
|
Ask TandemWorld
Got a question about NonStop ?
ASK Tandemworld
Keep up with us on Twitter @tandemworld
We are currently seeking skilled resources
across the EMEA region,
contact us for More Info
www.tandemworld.net
Visit the XYPRO
events calendar to
see where we will be and sign up for free webinars

DUST September 2018September
11, 2018Scottsdale,
AZEvent
Website >

OZTUG HPE NonStop Summit 2018 SydneySeptember
18, 2018410
Concord Road Rhodes NSW 2138Event
Website >

ATUG 2018September
19, 2018HPE
Customer Solution Center, Alpharetta, Ga.Event
Website >

OZTUG HPE NonStop Summit 2018 MelbourneSeptember
20, 2018Melbourne
- 353 Burwood Highway Forest Hill, VIC 3131Event
Website >

CTUG 2018September
26, 2018 September 27, 2018Hewlett–Packard
Enterprise Canada, 5150 Spectrum Way, Mississauga, OntarioEvent
Website >

MATUG 2018September
28, 2018Linthicum,
Maryland - DoubleTree by Hilton Hotel Baltimore-BWI AirportEvent
Website >

MexTUG 2018October
4, 2018Sheraton
Maria Isabel Hotel and Towers - MexicoEvent
Website >

NonStop Technical Boot Camp 2018November
11, 2018 November 14, 2018Hyatt
Regency San Francisco Airport - BurlingameEvent
Website >
Find out more about us at
www.tandemworld.net
August 2018 Sponsor

|
|
|























